Factor responsible to hinder the growth of risk-based authentication market is limited budget of small enterprises to spend on better security related software which could affect the usage of risk-based authentications. Nevertheless, an exponential increase is observed in the number of internet based application such as connected devices, concept of smart cities, smart grids, and more. Also, adoption of risk-based authentication among the high industry verticals is fueling the demand of the risk-based authentications market with varied growth opportunities in the forthcoming period.
The "Global Risk-based Authentication Market Analysis to 2028" is a specialized and in-depth study of the Risk-based authentication industry with a focus on the global market trend. The report aims to provide an overview of global Risk-based authentication market with detailed market segmentation on the basis of component, deployment model, technology, security policy, application, end users, and geography. The global Risk-based authentication market is expected to witness high growth during the forecast period. The report provides key statistics on the market status of the leading market players and offers key trends and opportunities in the Risk-based Authentication market.
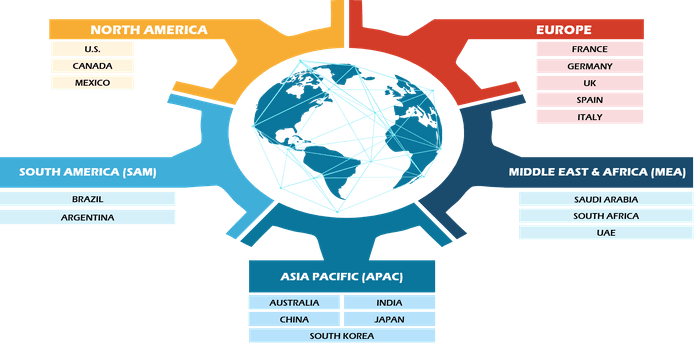
The report provides a detailed overview of the industry including both qualitative and quantitative information. It provides overview and forecast of the global risk-based authentication market based on component, deployment model, technology, security policy, application, and end users. It also provides market size and forecast till 2028 for overall Risk-based authentication market with respect to five major regions, namely; North America, Europe, Asia-Pacific (APAC), Middle East and Africa (MEA) and South America (SAM). The market by each region is later sub-segmented by respective countries and segments. The report covers analysis and forecast of 16 countries globally along with current trend and opportunities prevailing in the region.
Besides this, the report analyzes factors affecting market from both demand and supply side and further evaluates market dynamics effecting the market during the forecast period i.e., drivers, restraints, opportunities, and future trend. The report also provides exhaustive PEST analysis for all five regions namely; North America, Europe, APAC, MEA and South America after evaluating political, economic, social and technological factors effecting the market in these regions.
Also, key Risk-based authentication market players influencing the market are profiled in the study along with their SWOT analysis and market strategies. The report also focuses on leading industry players with information such as company profiles, products and services offered, financial information of last 3 years, key development in past five years. Some of the key players influencing the market are the list of companies for Risk-based authentication market are Crossmatch, IBM Corporation, Oracle corporation, GURUCUL, Micro Focus International Plc, Equifax Inc., Gemalto N.V., RSA Security LLC, Ping Identity, and CA Technologies among others.
REGIONAL FRAMEWORK

Have a question?

Naveen
Naveen will walk you through a 15-minute call to present the report’s content and answer all queries if you have any.
 Speak to Analyst
Speak to Analyst
- Sample PDF showcases the content structure and the nature of the information with qualitative and quantitative analysis.
- Sample PDF showcases the content structure and the nature of the information with qualitative and quantitative analysis.

Report Coverage
Revenue forecast, Company Analysis, Industry landscape, Growth factors, and Trends
Segment Covered
This text is related
to segments covered.

Regional Scope
North America, Europe, Asia Pacific, Middle East & Africa, South & Central America
Country Scope
This text is related
to country scope.
1. Crossmatch
2. IBM Corporation
3. Oracle corporation
4. GURUCUL
5. Micro Focus International Plc
6. Equifax Inc.
7. Gemalto N.V.
8. RSA Security LLC
9. Ping Identity
10. CA Technologies
The Insight Partners performs research in 4 major stages: Data Collection & Secondary Research, Primary Research, Data Analysis and Data Triangulation & Final Review.
- Data Collection and Secondary Research:
As a market research and consulting firm operating from a decade, we have published many reports and advised several clients across the globe. First step for any study will start with an assessment of currently available data and insights from existing reports. Further, historical and current market information is collected from Investor Presentations, Annual Reports, SEC Filings, etc., and other information related to company’s performance and market positioning are gathered from Paid Databases (Factiva, Hoovers, and Reuters) and various other publications available in public domain.
Several associations trade associates, technical forums, institutes, societies and organizations are accessed to gain technical as well as market related insights through their publications such as research papers, blogs and press releases related to the studies are referred to get cues about the market. Further, white papers, journals, magazines, and other news articles published in the last 3 years are scrutinized and analyzed to understand the current market trends.
- Primary Research:
The primarily interview analysis comprise of data obtained from industry participants interview and answers to survey questions gathered by in-house primary team.
For primary research, interviews are conducted with industry experts/CEOs/Marketing Managers/Sales Managers/VPs/Subject Matter Experts from both demand and supply side to get a 360-degree view of the market. The primary team conducts several interviews based on the complexity of the markets to understand the various market trends and dynamics which makes research more credible and precise.
A typical research interview fulfils the following functions:
- Provides first-hand information on the market size, market trends, growth trends, competitive landscape, and outlook
- Validates and strengthens in-house secondary research findings
- Develops the analysis team’s expertise and market understanding
Primary research involves email interactions and telephone interviews for each market, category, segment, and sub-segment across geographies. The participants who typically take part in such a process include, but are not limited to:
- Industry participants: VPs, business development managers, market intelligence managers and national sales managers
- Outside experts: Valuation experts, research analysts and key opinion leaders specializing in the electronics and semiconductor industry.
Below is the breakup of our primary respondents by company, designation, and region:
Once we receive the confirmation from primary research sources or primary respondents, we finalize the base year market estimation and forecast the data as per the macroeconomic and microeconomic factors assessed during data collection.
- Data Analysis:
Once data is validated through both secondary as well as primary respondents, we finalize the market estimations by hypothesis formulation and factor analysis at regional and country level.
- 3.1 Macro-Economic Factor Analysis:
We analyse macroeconomic indicators such the gross domestic product (GDP), increase in the demand for goods and services across industries, technological advancement, regional economic growth, governmental policies, the influence of COVID-19, PEST analysis, and other aspects. This analysis aids in setting benchmarks for various nations/regions and approximating market splits. Additionally, the general trend of the aforementioned components aid in determining the market's development possibilities.
- 3.2 Country Level Data:
Various factors that are especially aligned to the country are taken into account to determine the market size for a certain area and country, including the presence of vendors, such as headquarters and offices, the country's GDP, demand patterns, and industry growth. To comprehend the market dynamics for the nation, a number of growth variables, inhibitors, application areas, and current market trends are researched. The aforementioned elements aid in determining the country's overall market's growth potential.
- 3.3 Company Profile:
The “Table of Contents” is formulated by listing and analyzing more than 25 - 30 companies operating in the market ecosystem across geographies. However, we profile only 10 companies as a standard practice in our syndicate reports. These 10 companies comprise leading, emerging, and regional players. Nonetheless, our analysis is not restricted to the 10 listed companies, we also analyze other companies present in the market to develop a holistic view and understand the prevailing trends. The “Company Profiles” section in the report covers key facts, business description, products & services, financial information, SWOT analysis, and key developments. The financial information presented is extracted from the annual reports and official documents of the publicly listed companies. Upon collecting the information for the sections of respective companies, we verify them via various primary sources and then compile the data in respective company profiles. The company level information helps us in deriving the base number as well as in forecasting the market size.
- 3.4 Developing Base Number:
Aggregation of sales statistics (2020-2022) and macro-economic factor, and other secondary and primary research insights are utilized to arrive at base number and related market shares for 2022. The data gaps are identified in this step and relevant market data is analyzed, collected from paid primary interviews or databases. On finalizing the base year market size, forecasts are developed on the basis of macro-economic, industry and market growth factors and company level analysis.
- Data Triangulation and Final Review:
The market findings and base year market size calculations are validated from supply as well as demand side. Demand side validations are based on macro-economic factor analysis and benchmarks for respective regions and countries. In case of supply side validations, revenues of major companies are estimated (in case not available) based on industry benchmark, approximate number of employees, product portfolio, and primary interviews revenues are gathered. Further revenue from target product/service segment is assessed to avoid overshooting of market statistics. In case of heavy deviations between supply and demand side values, all thes steps are repeated to achieve synchronization.
We follow an iterative model, wherein we share our research findings with Subject Matter Experts (SME’s) and Key Opinion Leaders (KOLs) until consensus view of the market is not formulated – this model negates any drastic deviation in the opinions of experts. Only validated and universally acceptable research findings are quoted in our reports.
We have important check points that we use to validate our research findings – which we call – data triangulation, where we validate the information, we generate from secondary sources with primary interviews and then we re-validate with our internal data bases and Subject matter experts. This comprehensive model enables us to deliver high quality, reliable data in shortest possible time.
Trends and growth analysis reports related to Risk-based Authentication Market

Apr 2024
Engineering Professional Services Market
Size and Forecast (2021 - 2031), Global and Regional Share, Trend, and Growth Opportunity Analysis Report Coverage: By Type (Consulting, Non-Consulting), Service Type (Designing and Construction, ESG, Program Management, Others), Sector (Private, Public), Vertical (Advanced Manufacturing, Infrastructure, Energy and Utilities, Environmental, Transportation, Others), Advanced Manufacturing (Data Center, Life Sciences, Electronics, and Semiconductor, EV and EV Battery, Others), Infrastructure (Buildings and Cities, Health Infrastructure, Telecommunication Infrastructure, Others), Energy And Utilities (Renewables, Energy Storage, Transmission and Distribution), Transportation (Aviation, Highways and Bridges, Ports and Maritime, Rail and Transit), Water (Water, Wastewater), and Geography (Americas, Europe, Asia Pacific and Middle East and Africa)

Apr 2024
Virtual Reality Puzzle Games Market
Size and Forecast (2020 - 2030), Global and Regional Share, Trend, and Growth Opportunity Analysis Report Coverage: By Age (18 to 34 Years, Above 35 Years, 13 to 17 Years, and Upto 12 Years), Player Type (Single Player and Multi Player), and End Users (Individuals and Professionals)

Apr 2024
Inspection Software for Government Services Market
Size and Forecast (2020 - 2030), Global and Regional Share, Trend, and Growth Opportunity Analysis Report Coverage: By Component (Software and Services), Services (Implementation and Deployment, Support and Maintenance, Training, and Consulting), Deployment (Cloud and On-premises), Application (Permitting and Licensing Management, Inspection and Scheduling Management, Contract Management, and Others), and End User (Local Government, State Government, and Federal Government)

Apr 2024
Spend Analytics for Electronics and Semiconductor Market
Size and Forecasts (2020 - 2030), Global and Regional Share, Trend, and Growth Opportunity Analysis By Component (Software and Service), Type (Descriptive Analytics, Predictive Analytics, and Prescriptive Analytics), Deployment (On-premise and Cloud), and Application (Financial Management, Risk Management, Governance and Compliance Management, Supplier Sourcing and Performance Management, Demand and Supply Forecasting, and Others)

Apr 2024
Photonic Design Automation Market
Size and Forecasts (2020 - 2030), Global and Regional Share, Trends, and Growth Opportunity Analysis Report Coverage: By Component (Solution and Service), Deployment (On-Premise and Cloud), Organization Size (SMEs and Large Enterprises), and Application (Academic Research and Industrial Research & Manufacturing)

Apr 2024
Voice-based Payments Market
Size and Forecast (2020 - 2030), Global and Regional Share, Trend, and Growth Opportunity Analysis Report Coverage: By Component (Hardware and Software), By Enterprise Size (Large Enterprises and Small and Medium-Sized Enterprises), By Industry (BFSI, Automotive, Healthcare, Retail, Government, and Others), and by Geography

Apr 2024
Private 5G Network Market
Size and Forecasts (2020 - 2030), Global and Regional Share, Trends, and Growth Opportunity Analysis Report Coverage: By Component (Hardware, Software, and Services); Frequency (Sub-6 GHz and mmWave), End User (Manufacturing, Energy and Utilities, Automotive, Military and Defense, Government and Public Safety, and Others)

Apr 2024
Unified Threat Management Market
Size and Forecasts (2020 - 2030), Global and Regional Share, Trends, and Growth Opportunity Analysis Report Coverage: By Component (Solution and Services); Deployment (Cloud and On-Premise); Enterprise Size (Large Enterprises and SMEs); and End Users (BFSI, Manufacturing, Healthcare, Retail, Government, IT & Telecom, and Others)