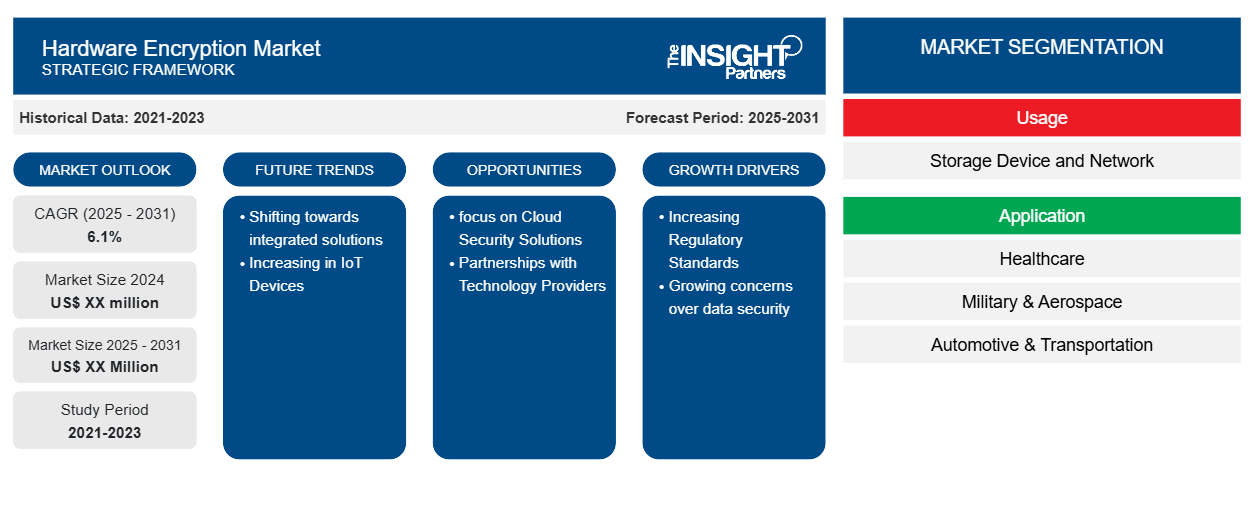
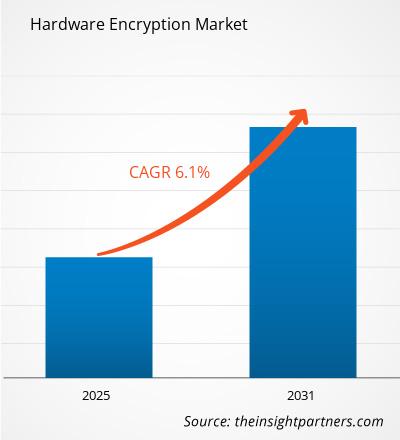
The Hardware Encryption Market is expected to register a CAGR of 6.1% from 2025 to 2031, with a market size expanding from US$ XX million in 2024 to US$ XX Million by 2031.
The report is segmented by Usage (Storage Device and Network), Application (Healthcare, Military & Aerospace, Automotive & Transportation, and IT & Telecom), and End-user (Industrial, Commercial, Residential, Healthcare, and Government Agencies). The global analysis is further broken-down at regional level and major countries. The report offers the value in USD for the above analysis and segments
Purpose of the Report
The report Hardware Encryption Market by The Insight Partners aims to describe the present landscape and future growth, top driving factors, challenges, and opportunities. This will provide insights to various business stakeholders, such as:
- Technology Providers/Manufacturers: To understand the evolving market dynamics and know the potential growth opportunities, enabling them to make informed strategic decisions.
- Investors: To conduct a comprehensive trend analysis regarding the market growth rate, market financial projections, and opportunities that exist across the value chain.
- Regulatory bodies: To regulate policies and police activities in the market with the aim of minimizing abuse, preserving investor trust and confidence, and upholding the integrity and stability of the market.
Hardware Encryption Market Segmentation
Usage
- Storage Device and Network
Application
- Healthcare
- Military & Aerospace
- Automotive & Transportation
- IT & Telecom
End-user
- Industrial
- Commercial
- Residential
- Healthcare
- Government Agencies
Geography
- North America
- Europe
- Asia-Pacific
- South and Central America
- Middle East and Africa
You will get customization on any report - free of charge - including parts of this report, or country-level analysis, Excel Data pack, as well as avail great offers and discounts for start-ups & universities
Hardware Encryption Market: Strategic Insights
- Get Top Key Market Trends of this report.This FREE sample will include data analysis, ranging from market trends to estimates and forecasts.
Hardware Encryption Market Growth Drivers
- Increasing Regulatory Standards: The rise in regulatory standards and data privacy compliance requirements is a major driving force behind the hardware encryption market. Organizations are forced to implement robust encryption solutions to protect sensitive data and meet legal obligations, leading to increased adoption of hardware encryption technologies.
- Growing concerns over data security: Heightened concerns regarding data breaches and cyber threats are driving demand for hardware encryption. As organizations seek to safeguard their sensitive information, hardware encryption provides a reliable solution that enhances data protection and mitigates risks associated with unauthorized access.
Hardware Encryption Market Future Trends
- Shifting towards integrated solutions: There is a growing trend towards integrated hardware encryption solutions, where several security features are offered in one. Organizations seek all-inclusive solutions offering encryption in addition to other security measures like access control and authentication for the overall protection of data.
- Increasing in IoT Devices: The rapid growth of IoT devices is one of the prime drivers for the hardware encryption market. As connected devices continue to grow in exponential proportions, generating large amounts of sensitive data, there's an urgent need for hardware encryption to secure communication and data integrity across IoT ecosystems.
Hardware Encryption Market Opportunities
- focus on Cloud Security Solutions: The increasing trend of cloud computing opens doors for hardware encryption providers. As businesses transition to the cloud, there is a need for better encryption solutions to protect their data stored in cloud environments, which further increases demand for hardware-based encryption technologies.
- Partnerships with Technology Providers: New opportunities in the form of strategic partnerships between hardware encryption vendors and technology providers may arise. Integrated solutions that improve security features and interoperability can be developed, thus appealing to a wider section of customers.
Hardware Encryption Market Regional Insights
The regional trends and factors influencing the Hardware Encryption Market throughout the forecast period have been thoroughly explained by the analysts at The Insight Partners. This section also discusses Hardware Encryption Market segments and geography across North America, Europe, Asia Pacific, Middle East and Africa, and South and Central America.
- Get the Regional Specific Data for Hardware Encryption Market
Hardware Encryption Market Report Scope
| Report Attribute | Details |
|---|---|
| Market size in 2024 | US$ XX million |
| Market Size by 2031 | US$ XX Million |
| Global CAGR (2025 - 2031) | 6.1% |
| Historical Data | 2021-2023 |
| Forecast period | 2025-2031 |
| Segments Covered |
By Usage
|
| Regions and Countries Covered | North America
|
| Market leaders and key company profiles |
Hardware Encryption Market Players Density: Understanding Its Impact on Business Dynamics
The Hardware Encryption Market is growing rapidly, driven by increasing end-user demand due to factors such as evolving consumer preferences, technological advancements, and greater awareness of the product's benefits. As demand rises, businesses are expanding their offerings, innovating to meet consumer needs, and capitalizing on emerging trends, which further fuels market growth.
Market players density refers to the distribution of firms or companies operating within a particular market or industry. It indicates how many competitors (market players) are present in a given market space relative to its size or total market value.
Major Companies operating in the Hardware Encryption Market are:
- E-Security (Thales)
- Gemalto NV
- Kanguru Solutions
- Kingston Technology Corp
- Maxim Integrated
Disclaimer: The companies listed above are not ranked in any particular order.
- Get the Hardware Encryption Market top key players overview
Key Selling Points
- Comprehensive Coverage: The report comprehensively covers the analysis of products, services, types, and end users of the Hardware Encryption Market, providing a holistic landscape.
- Expert Analysis: The report is compiled based on the in-depth understanding of industry experts and analysts.
- Up-to-date Information: The report assures business relevance due to its coverage of recent information and data trends.
- Customization Options: This report can be customized to cater to specific client requirements and suit the business strategies aptly.
The research report on the Hardware Encryption Market can, therefore, help spearhead the trail of decoding and understanding the industry scenario and growth prospects. Although there can be a few valid concerns, the overall benefits of this report tend to outweigh the disadvantages.
Frequently Asked Questions
What are the deliverable formats of the market report?
The report can be delivered in PDF/PPT format; we can also share excel dataset based on the request
What are the options available for the customization of this report?
Some of the customization options available based on the request are an additional 3-5 company profiles and country-specific analysis of 3-5 countries of your choice. Customizations are to be requested/discussed before making final order confirmation# as our team would review the same and check the feasibility
What is the expected CAGR of the hardware encryption market
The Hardware Encryption Market is estimated to witness a CAGR of 6.1% from 2023 to 2038
What are the driving factors impacting the global hardware encryption market?
Increasing Regulatory Standards, Growing concerns over data security, Increasing in IoT Devices
What are the future trends of the hardware encryption market?
Shifting towards integrated solutions
- Historical Analysis (2 Years), Base Year, Forecast (7 Years) with CAGR
- PEST and SWOT Analysis
- Market Size Value / Volume - Global, Regional, Country
- Industry and Competitive Landscape
- Excel Dataset
Testimonials
Reason to Buy
- Informed Decision-Making
- Understanding Market Dynamics
- Competitive Analysis
- Identifying Emerging Markets
- Customer Insights
- Market Forecasts
- Risk Mitigation
- Boosting Operational Efficiency
- Strategic Planning
- Investment Justification
- Tracking Industry Innovations
- Aligning with Regulatory Trends
Yes! We provide a free sample of the report, which includes Report Scope (Table of Contents), report structure, and selected insights to help you assess the value of the full report. Please click on the "Download Sample" button or contact us to receive your copy.
Absolutely — analyst assistance is part of the package. You can connect with our analyst post-purchase to clarify report insights, methodology or discuss how the findings apply to your business needs.
Once your order is successfully placed, you will receive a confirmation email along with your invoice.
• For published reports: You’ll receive access to the report within 4–6 working hours via a secured email sent to your email.
• For upcoming reports: Your order will be recorded as a pre-booking. Our team will share the estimated release date and keep you informed of any updates. As soon as the report is published, it will be delivered to your registered email.
We offer customization options to align the report with your specific objectives. Whether you need deeper insights into a particular region, industry segment, competitor analysis, or data cut, our research team can tailor the report accordingly. Please share your requirements with us, and we’ll be happy to provide a customized proposal or scope.
The report is available in either PDF format or as an Excel dataset, depending on the license you choose.
The PDF version provides the full analysis and visuals in a ready-to-read format. The Excel dataset includes all underlying data tables for easy manipulation and further analysis.
Please review the license options at checkout or contact us to confirm which formats are included with your purchase.
Our payment process is fully secure and PCI-DSS compliant.
We use trusted and encrypted payment gateways to ensure that all transactions are protected with industry-standard SSL encryption. Your payment details are never stored on our servers and are handled securely by certified third-party processors.
You can make your purchase with confidence, knowing your personal and financial information is safe with us.
Yes, we do offer special pricing for bulk purchases.
If you're interested in purchasing multiple reports, we’re happy to provide a customized bundle offer or volume-based discount tailored to your needs. Please contact our sales team with the list of reports you’re considering, and we’ll share a personalized quote.
Yes, absolutely.
Our team is available to help you make an informed decision. Whether you have questions about the report’s scope, methodology, customization options, or which license suits you best, we’re here to assist. Please reach out to us at sales@theinsightpartners.com, and one of our representatives will get in touch promptly.
Yes, a billing invoice will be automatically generated and sent to your registered email upon successful completion of your purchase.
If you need the invoice in a specific format or require additional details (such as company name, GST, or VAT information), feel free to contact us, and we’ll be happy to assist.
Yes, certainly.
If you encounter any difficulties accessing or receiving your report, our support team is ready to assist you. Simply reach out to us via email or live chat with your order information, and we’ll ensure the issue is resolved quickly so you can access your report without interruption.














The List of Companies
1. E-Security (Thales)
2. Gemalto NV
3. Kanguru Solutions
4. Kingston Technology Corp
5. Maxim Integrated
6. McAfee, LLC
7. Micron Technology, Inc.
8. Netapp
9. Samsung Electronics Co. Ltd.
10. Toshiba Corp






 Get Free Sample For
Get Free Sample For