The Digital Security Control Market is expected to register a CAGR of XX% from 2025 to 2031, with a market size expanding from US$ XX Million in 2024 to US$ XX Million by 2031.
The report is categorized by Component (Hardware, Software, Service) and further analyzes the market based on Application (Mobile Security and Telecommunication, Finance and Banking, Healthcare, Commercial). A comprehensive breakdown is provided at global, regional, and country levels for each of these key segments.
The report includes market size and forecasts across all segments, presenting values in USD. It also delivers key statistics on the current market status of leading players, along with insights into prevailing market trends and emerging opportunities.
The report Digital Security Control Market by The Insight Partners aims to describe the present landscape and future growth, top driving factors, challenges, and opportunities. This will provide insights to various business stakeholders, such as:
- Technology Providers/Manufacturers: To understand the evolving market dynamics and know the potential growth opportunities, enabling them to make informed strategic decisions.
- Investors: To conduct a comprehensive trend analysis regarding the market growth rate, market financial projections, and opportunities that exist across the value chain.
- Regulatory bodies: To regulate policies and police activities in the market with the aim of minimizing abuse, preserving investor trust and confidence, and upholding the integrity and stability of the market.
Digital Security Control Market Segmentation
Component- Hardware
- Software
- Service
- Mobile Security and Telecommunication
- Finance and Banking
- Healthcare
- Commercial
Strategic Insights
Digital Security Control Market Growth Drivers- Empowering Businesses with Robust Digital Security Solutions
- Safeguarding Your Data: The Future of Cybersecurity Innovation
- Building Trust: Enhancing Customer Confidence in Digital Transactions
- Rise of AI-Driven Cybersecurity Solutions Enhancing Protection
- Remote Work Boosts Demand for Advanced Digital Security Tools
- Blockchain Technology Revolutionizes Data Integrity and Security
- Empowering Small Businesses with Affordable Cybersecurity Solutions
- Innovative AI-Driven Tools for Enhanced Digital Threat Detection
- User-Friendly Security Apps for Everyday Consumers' Peace of Mind
Market Report Scope
Key Selling Points
- Comprehensive Coverage: The report comprehensively covers the analysis of products, services, types, and end users of the Digital Security Control Market, providing a holistic landscape.
- Expert Analysis: The report is compiled based on the in-depth understanding of industry experts and analysts.
- Up-to-date Information: The report assures business relevance due to its coverage of recent information and data trends.
- Customization Options: This report can be customized to cater to specific client requirements and suit the business strategies aptly.
The research report on the Digital Security Control Market can, therefore, help spearhead the trail of decoding and understanding the industry scenario and growth prospects. Although there can be a few valid concerns, the overall benefits of this report tend to outweigh the disadvantages.
REGIONAL FRAMEWORK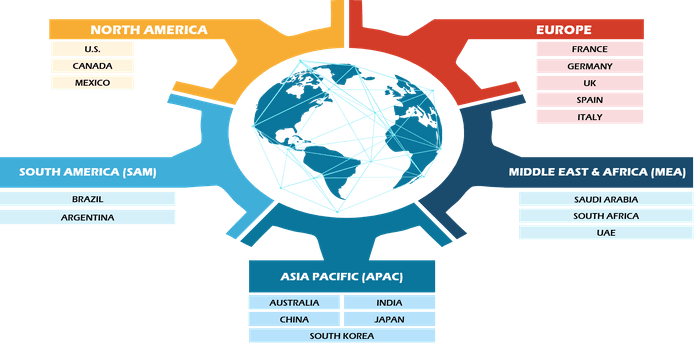
Have a question?

Naveen
Naveen will walk you through a 15-minute call to present the report’s content and answer all queries if you have any.
 Speak to Analyst
Speak to Analyst
- Sample PDF showcases the content structure and the nature of the information with qualitative and quantitative analysis.
- Request discounts available for Start-Ups & Universities
- Sample PDF showcases the content structure and the nature of the information with qualitative and quantitative analysis.
- Request discounts available for Start-Ups & Universities

Report Coverage
Revenue forecast, Company Analysis, Industry landscape, Growth factors, and Trends
Segment Covered
This text is related
to segments covered.

Regional Scope
North America, Europe, Asia Pacific, Middle East & Africa, South & Central America
Country Scope
This text is related
to country scope.
1. INTRODUCTION
1.1. SCOPE OF THE STUDY
1.2. THE INSIGHT PARTNERS RESEARCH REPORT GUIDANCE
1.3. MARKET SEGMENTATION
1.3.1Digital Security Control Market - By Component
1.3.2Digital Security Control Market - By Application
1.3.3Digital Security Control Market - By Region
1.3.3.1 By Country
2. KEY TAKEAWAYS
3. RESEARCH METHODOLOGY
4.DIGITAL SECURITY CONTROL MARKET LANDSCAPE
4.1.OVERVIEW
4.2.PORTER™S FIVE FORCES ANALYSIS
4.2.1Bargaining Power of Buyers
4.2.1Bargaining Power of Suppliers
4.2.1Threat of Substitute
4.2.1Threat of New Entrants
4.2.1Competitive Rivalry
4.3.ECOSYSTEM ANALYSIS
4.4.EXPERT OPINIONS
5.DIGITAL SECURITY CONTROL MARKET - KEY MARKET DYNAMICS
5.1.KEY MARKET DRIVERS
5.2.KEY MARKET RESTRAINTS
5.3.KEY MARKET OPPORTUNITIES
5.4.FUTURE TRENDS
5.5.IMPACT ANALYSIS OF DRIVERS AND RESTRAINTS
6.DIGITAL SECURITY CONTROL MARKET - GLOBAL MARKET ANALYSIS
6.1.DIGITAL SECURITY CONTROL - GLOBAL MARKET OVERVIEW
6.2.DIGITAL SECURITY CONTROL - GLOBAL MARKET AND FORECAST TO 2028
6.3.MARKET POSITIONING/MARKET SHARE
7.DIGITAL SECURITY CONTROL MARKET - REVENUE AND FORECASTS TO 2028- COMPONENT
7.1.OVERVIEW
7.2.COMPONENT MARKET FORECASTS AND ANALYSIS
7.3.HARDWARE
7.3.1.Overview
7.3.2.Hardware Market Forecast and Analysis
7.3.3.Smart Card Market
7.3.3.1.Overview
7.3.3.2.Smart Card Market Forecast and Analysis
7.3.4.Biometric Technologies Market
7.3.4.1.Overview
7.3.4.2.Biometric Technologies Market Forecast and Analysis
7.3.5.Security Tokens Market
7.3.5.1.Overview
7.3.5.2.Security Tokens Market Forecast and Analysis
7.4.SOFTWARE
7.4.1.Overview
7.4.2.Software Market Forecast and Analysis
7.4.3.Anit-Phishing Market
7.4.3.1.Overview
7.4.3.2.Anit-Phishing Market Forecast and Analysis
7.4.4.Authentication Market
7.4.4.1.Overview
7.4.4.2.Authentication Market Forecast and Analysis
7.4.5.Network Surveillance Market
7.4.5.1.Overview
7.4.5.2.Network Surveillance Market Forecast and Analysis
7.4.6.Security Management Market
7.4.6.1.Overview
7.4.6.2.Security Management Market Forecast and Analysis
7.4.7.Web Technologies Market
7.4.7.1.Overview
7.4.7.2.Web Technologies Market Forecast and Analysis
7.5.SERVICE
7.5.1.Overview
7.5.2.Service Market Forecast and Analysis
7.5.3.Two-Factor Authentication Market
7.5.3.1.Overview
7.5.3.2.Two-Factor Authentication Market Forecast and Analysis
7.5.4.Three-Factor Authentication Market
7.5.4.1.Overview
7.5.4.2.Three-Factor Authentication Market Forecast and Analysis
7.5.5.Four-Factor Authentication Market
7.5.5.1.Overview
7.5.5.2.Four-Factor Authentication Market Forecast and Analysis
8.DIGITAL SECURITY CONTROL MARKET - REVENUE AND FORECASTS TO 2028- APPLICATION
8.1.OVERVIEW
8.2.APPLICATION MARKET FORECASTS AND ANALYSIS
8.3.MOBILE SECURITY AND TELECOMMUNICATION
8.3.1.Overview
8.3.2.Mobile Security and Telecommunication Market Forecast and Analysis
8.4.FINANCE AND BANKING
8.4.1.Overview
8.4.2.Finance and Banking Market Forecast and Analysis
8.5.HEALTHCARE
8.5.1.Overview
8.5.2.Healthcare Market Forecast and Analysis
8.6.COMMERCIAL
8.6.1.Overview
8.6.2.Commercial Market Forecast and Analysis
8.7.OTHER
8.7.1.Overview
8.7.2.Other Market Forecast and Analysis
9.DIGITAL SECURITY CONTROL MARKET REVENUE AND FORECASTS TO 2028- GEOGRAPHICAL ANALYSIS
9.1.NORTH AMERICA
9.1.1North America Digital Security Control Market Overview
9.1.2North America Digital Security Control Market Forecasts and Analysis
9.1.3North America Digital Security Control Market Forecasts and Analysis - By Component
9.1.4North America Digital Security Control Market Forecasts and Analysis - By Application
9.1.5North America Digital Security Control Market Forecasts and Analysis - By Countries
9.1.5.1United States Digital Security Control Market
9.1.5.1.1United States Digital Security Control Market by Component
9.1.5.1.2United States Digital Security Control Market by Application
9.1.5.2Canada Digital Security Control Market
9.1.5.2.1Canada Digital Security Control Market by Component
9.1.5.2.2Canada Digital Security Control Market by Application
9.1.5.3Mexico Digital Security Control Market
9.1.5.3.1Mexico Digital Security Control Market by Component
9.1.5.3.2Mexico Digital Security Control Market by Application
9.2.EUROPE
9.2.1Europe Digital Security Control Market Overview
9.2.2Europe Digital Security Control Market Forecasts and Analysis
9.2.3Europe Digital Security Control Market Forecasts and Analysis - By Component
9.2.4Europe Digital Security Control Market Forecasts and Analysis - By Application
9.2.5Europe Digital Security Control Market Forecasts and Analysis - By Countries
9.2.5.1Germany Digital Security Control Market
9.2.5.1.1Germany Digital Security Control Market by Component
9.2.5.1.2Germany Digital Security Control Market by Application
9.2.5.2France Digital Security Control Market
9.2.5.2.1France Digital Security Control Market by Component
9.2.5.2.2France Digital Security Control Market by Application
9.2.5.3Italy Digital Security Control Market
9.2.5.3.1Italy Digital Security Control Market by Component
9.2.5.3.2Italy Digital Security Control Market by Application
9.2.5.4United Kingdom Digital Security Control Market
9.2.5.4.1United Kingdom Digital Security Control Market by Component
9.2.5.4.2United Kingdom Digital Security Control Market by Application
9.2.5.5Russia Digital Security Control Market
9.2.5.5.1Russia Digital Security Control Market by Component
9.2.5.5.2Russia Digital Security Control Market by Application
9.2.5.6Rest of Europe Digital Security Control Market
9.2.5.6.1Rest of Europe Digital Security Control Market by Component
9.2.5.6.2Rest of Europe Digital Security Control Market by Application
9.3.ASIA-PACIFIC
9.3.1Asia-Pacific Digital Security Control Market Overview
9.3.2Asia-Pacific Digital Security Control Market Forecasts and Analysis
9.3.3Asia-Pacific Digital Security Control Market Forecasts and Analysis - By Component
9.3.4Asia-Pacific Digital Security Control Market Forecasts and Analysis - By Application
9.3.5Asia-Pacific Digital Security Control Market Forecasts and Analysis - By Countries
9.3.5.1Australia Digital Security Control Market
9.3.5.1.1Australia Digital Security Control Market by Component
9.3.5.1.2Australia Digital Security Control Market by Application
9.3.5.2China Digital Security Control Market
9.3.5.2.1China Digital Security Control Market by Component
9.3.5.2.2China Digital Security Control Market by Application
9.3.5.3India Digital Security Control Market
9.3.5.3.1India Digital Security Control Market by Component
9.3.5.3.2India Digital Security Control Market by Application
9.3.5.4Japan Digital Security Control Market
9.3.5.4.1Japan Digital Security Control Market by Component
9.3.5.4.2Japan Digital Security Control Market by Application
9.3.5.5South Korea Digital Security Control Market
9.3.5.5.1South Korea Digital Security Control Market by Component
9.3.5.5.2South Korea Digital Security Control Market by Application
9.4.MIDDLE EAST AND AFRICA
9.4.1Middle East and Africa Digital Security Control Market Overview
9.4.2Middle East and Africa Digital Security Control Market Forecasts and Analysis
9.4.3Middle East and Africa Digital Security Control Market Forecasts and Analysis - By Component
9.4.4Middle East and Africa Digital Security Control Market Forecasts and Analysis - By Application
9.4.5Middle East and Africa Digital Security Control Market Forecasts and Analysis - By Countries
9.4.5.1South Africa Digital Security Control Market
9.4.5.1.1South Africa Digital Security Control Market by Component
9.4.5.1.2South Africa Digital Security Control Market by Application
9.4.5.2Saudi Arabia Digital Security Control Market
9.4.5.2.1Saudi Arabia Digital Security Control Market by Component
9.4.5.2.2Saudi Arabia Digital Security Control Market by Application
9.4.5.3U.A.E Digital Security Control Market
9.4.5.3.1U.A.E Digital Security Control Market by Component
9.4.5.3.2U.A.E Digital Security Control Market by Application
9.4.5.4Rest of Middle East and Africa Digital Security Control Market
9.4.5.4.1Rest of Middle East and Africa Digital Security Control Market by Component
9.4.5.4.2Rest of Middle East and Africa Digital Security Control Market by Application
9.5.SOUTH AND CENTRAL AMERICA
9.5.1South and Central America Digital Security Control Market Overview
9.5.2South and Central America Digital Security Control Market Forecasts and Analysis
9.5.3South and Central America Digital Security Control Market Forecasts and Analysis - By Component
9.5.4South and Central America Digital Security Control Market Forecasts and Analysis - By Application
9.5.5South and Central America Digital Security Control Market Forecasts and Analysis - By Countries
9.5.5.1Brazil Digital Security Control Market
9.5.5.1.1Brazil Digital Security Control Market by Component
9.5.5.1.2Brazil Digital Security Control Market by Application
9.5.5.2Argentina Digital Security Control Market
9.5.5.2.1Argentina Digital Security Control Market by Component
9.5.5.2.2Argentina Digital Security Control Market by Application
9.5.5.3Rest of South and Central America Digital Security Control Market
9.5.5.3.1Rest of South and Central America Digital Security Control Market by Component
9.5.5.3.2Rest of South and Central America Digital Security Control Market by Application
10.INDUSTRY LANDSCAPE
10.1.MERGERS AND ACQUISITIONS
10.2.AGREEMENTS, COLLABORATIONS AND JOIN VENTURES
10.3.NEW PRODUCT LAUNCHES
10.4.EXPANSIONS AND OTHER STRATEGIC DEVELOPMENTS
11.DIGITAL SECURITY CONTROL MARKET, KEY COMPANY PROFILES
11.1.GEMALTO NV
11.1.1.Key Facts
11.1.2.Business Description
11.1.3.Products and Services
11.1.4.Financial Overview
11.1.5.SWOT Analysis
11.1.6.Key Developments
11.2.FIREEYE, INC.
11.2.1.Key Facts
11.2.2.Business Description
11.2.3.Products and Services
11.2.4.Financial Overview
11.2.5.SWOT Analysis
11.2.6.Key Developments
11.3.OBERTHUR TECHNOLOGIES
11.3.1.Key Facts
11.3.2.Business Description
11.3.3.Products and Services
11.3.4.Financial Overview
11.3.5.SWOT Analysis
11.3.6.Key Developments
11.4.SAFENET, INC.
11.4.1.Key Facts
11.4.2.Business Description
11.4.3.Products and Services
11.4.4.Financial Overview
11.4.5.SWOT Analysis
11.4.6.Key Developments
11.5.RSA SECURITY LLC
11.5.1.Key Facts
11.5.2.Business Description
11.5.3.Products and Services
11.5.4.Financial Overview
11.5.5.SWOT Analysis
11.5.6.Key Developments
11.6.VASCO DATA SECURITY INTERNATIONAL, INC.
11.6.1.Key Facts
11.6.2.Business Description
11.6.3.Products and Services
11.6.4.Financial Overview
11.6.5.SWOT Analysis
11.6.6.Key Developments
11.7.3M
11.7.1.Key Facts
11.7.2.Business Description
11.7.3.Products and Services
11.7.4.Financial Overview
11.7.5.SWOT Analysis
11.7.6.Key Developments
11.8.NEC CORPORATION
11.8.1.Key Facts
11.8.2.Business Description
11.8.3.Products and Services
11.8.4.Financial Overview
11.8.5.SWOT Analysis
11.8.6.Key Developments
11.9.MORPHO S.A.S
11.9.1.Key Facts
11.9.2.Business Description
11.9.3.Products and Services
11.9.4.Financial Overview
11.9.5.SWOT Analysis
11.9.6.Key Developments
11.10.HID GLOBAL (ACTIVIDENTITY, INC.)
11.10.1.Key Facts
11.10.2.Business Description
11.10.3.Products and Services
11.10.4.Financial Overview
11.10.5.SWOT Analysis
11.10.6.Key Developments
12.APPENDIX
12.1.ABOUT THE INSIGHT PARTNERS
12.2.GLOSSARY OF TERMS
Yes! We provide a free sample of the report, which includes Report Scope (Table of Contents), report structure, and selected insights to help you assess the value of the full report. Please click on the "Download Sample" button or contact us to receive your copy.
Absolutely - analyst assistance is part of the package. You can connect with our analyst post-purchase to clarify report insights, methodology or discuss how the findings apply to your business needs.
Once your order is successfully placed, you will receive a confirmation email along with your invoice.
• For published reports: You'll receive access to the report within 4-6 working hours via a secured email sent to your email.
• For upcoming reports: Your order will be recorded as a pre-booking. Our team will share the estimated release date and keep you informed of any updates. As soon as the report is published, it will be delivered to your registered email.
We offer customization options to align the report with your specific objectives. Whether you need deeper insights into a particular region, industry segment, competitor analysis, or data cut, our research team can tailor the report accordingly. Please share your requirements with us, and we'll be happy to provide a customized proposal or scope.
The report is available in either PDF format or as an Excel dataset, depending on the license you choose.
The PDF version provides the full analysis and visuals in a ready-to-read format. The Excel dataset includes all underlying data tables for easy manipulation and further analysis.
Please review the license options at checkout or contact us to confirm which formats are included with your purchase.
Our payment process is fully secure and PCI-DSS compliant.
We use trusted and encrypted payment gateways to ensure that all transactions are protected with industry-standard SSL encryption. Your payment details are never stored on our servers and are handled securely by certified third-party processors.
You can make your purchase with confidence, knowing your personal and financial information is safe with us.
Yes, we do offer special pricing for bulk purchases.
If you're interested in purchasing multiple reports, we're happy to provide a customized bundle offer or volume-based discount tailored to your needs. Please contact our sales team with the list of reports you're considering, and we'll share a personalized quote.
Yes, absolutely.
Our team is available to help you make an informed decision. Whether you have questions about the report's scope, methodology, customization options, or which license suits you best, we're here to assist. Please reach out to us at sales@theinsightpartners.com, and one of our representatives will get in touch promptly.
Yes, a billing invoice will be automatically generated and sent to your registered email upon successful completion of your purchase.
If you need the invoice in a specific format or require additional details (such as company name, GST, or VAT information), feel free to contact us, and we'll be happy to assist.
Yes, certainly.
If you encounter any difficulties accessing or receiving your report, our support team is ready to assist you. Simply reach out to us via email or live chat with your order information, and we'll ensure the issue is resolved quickly so you can access your report without interruption.
The Insight Partners performs research in 4 major stages: Data Collection & Secondary Research, Primary Research, Data Analysis and Data Triangulation & Final Review.
- Data Collection and Secondary Research:
As a market research and consulting firm operating from a decade, we have published many reports and advised several clients across the globe. First step for any study will start with an assessment of currently available data and insights from existing reports. Further, historical and current market information is collected from Investor Presentations, Annual Reports, SEC Filings, etc., and other information related to company’s performance and market positioning are gathered from Paid Databases (Factiva, Hoovers, and Reuters) and various other publications available in public domain.
Several associations trade associates, technical forums, institutes, societies and organizations are accessed to gain technical as well as market related insights through their publications such as research papers, blogs and press releases related to the studies are referred to get cues about the market. Further, white papers, journals, magazines, and other news articles published in the last 3 years are scrutinized and analyzed to understand the current market trends.
- Primary Research:
The primarily interview analysis comprise of data obtained from industry participants interview and answers to survey questions gathered by in-house primary team.
For primary research, interviews are conducted with industry experts/CEOs/Marketing Managers/Sales Managers/VPs/Subject Matter Experts from both demand and supply side to get a 360-degree view of the market. The primary team conducts several interviews based on the complexity of the markets to understand the various market trends and dynamics which makes research more credible and precise.
A typical research interview fulfils the following functions:
- Provides first-hand information on the market size, market trends, growth trends, competitive landscape, and outlook
- Validates and strengthens in-house secondary research findings
- Develops the analysis team’s expertise and market understanding
Primary research involves email interactions and telephone interviews for each market, category, segment, and sub-segment across geographies. The participants who typically take part in such a process include, but are not limited to:
- Industry participants: VPs, business development managers, market intelligence managers and national sales managers
- Outside experts: Valuation experts, research analysts and key opinion leaders specializing in the electronics and semiconductor industry.
Below is the breakup of our primary respondents by company, designation, and region:
Once we receive the confirmation from primary research sources or primary respondents, we finalize the base year market estimation and forecast the data as per the macroeconomic and microeconomic factors assessed during data collection.
- Data Analysis:
Once data is validated through both secondary as well as primary respondents, we finalize the market estimations by hypothesis formulation and factor analysis at regional and country level.
- 3.1 Macro-Economic Factor Analysis:
We analyse macroeconomic indicators such the gross domestic product (GDP), increase in the demand for goods and services across industries, technological advancement, regional economic growth, governmental policies, the influence of COVID-19, PEST analysis, and other aspects. This analysis aids in setting benchmarks for various nations/regions and approximating market splits. Additionally, the general trend of the aforementioned components aid in determining the market's development possibilities.
- 3.2 Country Level Data:
Various factors that are especially aligned to the country are taken into account to determine the market size for a certain area and country, including the presence of vendors, such as headquarters and offices, the country's GDP, demand patterns, and industry growth. To comprehend the market dynamics for the nation, a number of growth variables, inhibitors, application areas, and current market trends are researched. The aforementioned elements aid in determining the country's overall market's growth potential.
- 3.3 Company Profile:
The “Table of Contents” is formulated by listing and analyzing more than 25 - 30 companies operating in the market ecosystem across geographies. However, we profile only 10 companies as a standard practice in our syndicate reports. These 10 companies comprise leading, emerging, and regional players. Nonetheless, our analysis is not restricted to the 10 listed companies, we also analyze other companies present in the market to develop a holistic view and understand the prevailing trends. The “Company Profiles” section in the report covers key facts, business description, products & services, financial information, SWOT analysis, and key developments. The financial information presented is extracted from the annual reports and official documents of the publicly listed companies. Upon collecting the information for the sections of respective companies, we verify them via various primary sources and then compile the data in respective company profiles. The company level information helps us in deriving the base number as well as in forecasting the market size.
- 3.4 Developing Base Number:
Aggregation of sales statistics (2020-2022) and macro-economic factor, and other secondary and primary research insights are utilized to arrive at base number and related market shares for 2022. The data gaps are identified in this step and relevant market data is analyzed, collected from paid primary interviews or databases. On finalizing the base year market size, forecasts are developed on the basis of macro-economic, industry and market growth factors and company level analysis.
- Data Triangulation and Final Review:
The market findings and base year market size calculations are validated from supply as well as demand side. Demand side validations are based on macro-economic factor analysis and benchmarks for respective regions and countries. In case of supply side validations, revenues of major companies are estimated (in case not available) based on industry benchmark, approximate number of employees, product portfolio, and primary interviews revenues are gathered. Further revenue from target product/service segment is assessed to avoid overshooting of market statistics. In case of heavy deviations between supply and demand side values, all thes steps are repeated to achieve synchronization.
We follow an iterative model, wherein we share our research findings with Subject Matter Experts (SME’s) and Key Opinion Leaders (KOLs) until consensus view of the market is not formulated – this model negates any drastic deviation in the opinions of experts. Only validated and universally acceptable research findings are quoted in our reports.
We have important check points that we use to validate our research findings – which we call – data triangulation, where we validate the information, we generate from secondary sources with primary interviews and then we re-validate with our internal data bases and Subject matter experts. This comprehensive model enables us to deliver high quality, reliable data in shortest possible time.

Mar 2026
Defense and Aerospace NAND and NOR Flash Memory Market
Size and Forecast (2021 - 2031), Global and Regional Share, Trend, and Growth Opportunity Analysis Report Coverage: By Flash Memory Type (NAND Flash Memory and NOR Flash Memory), NAND Flash Memory (SLC, MLC, TLC, and Others), NOR Flash Memory (Parallel NOR and Serial NOR), NAND Flash Memory Architecture (2D NAND and 3D NAND), NOR Flash Memory Density (Upto 2 MB, 4 MB to 64 MB, 128 MB to 512 MB, and Greater than 1 GB), NAND Flash Memory Density (Upto 2 GB, 4 GB to 64 GB, 128 GB to 512 GB, and Above 1 Tb), and Region (North America, Europe, Asia Pacific, Middle East and Africa, and South and Central America)

Mar 2026
Differential-Pressure Mass Flow Controller Market
Size and Forecast (2021 - 2031), Global and Regional Share, Trend, and Growth Opportunity Analysis Report Coverage: By Flow Rate (Low, Medium, and High), Application (Semiconductors, Food and Beverages Industry, Chemicals, Pharmaceutical and Healthcare Industry, Oil and Gas, and Others), and Geography (North America, Europe, Asia Pacific, Middle East and Africa, and South and Central America)

Mar 2026
Coriolis Mass Flow Controller Market
Size and Forecast (2021 - 2031), Global and Regional Share, Trend, and Growth Opportunity Analysis Report Coverage: By Flow Rate (Low, Medium and High), Application (Semiconductors, Food and Beverages Industry, Chemicals, Pharmaceutical and Healthcare Industry, Oil and Gas, and Others), and Geography (North America, Europe, Asia Pacific, Middle East and Africa, and South and Central America)

Mar 2026
Monoblock Refrigeration Unit for Cold Room Market
Size and Forecast (2021 - 2031), Global and Regional Share, Trend, and Growth Opportunity Analysis Report Coverage: By Mounting Type (Wall Mounted and Ceiling Mounted), Capacity [Between Ten and Thirty Cubic Meters (10-30 cu m), Less than Ten Cubic Meters (less than 10 cu m), and Greater than Thirty Cubic Meters (Greater than 30 cu m)], End-User Industry (Food Retail, HoReCa, Cold Chain Logistics, Pharmaceutical or Healthcare, and Others), and Geography (North America, Europe, Asia Pacific, Middle East & Africa, and South & Central America)

Mar 2026
Parallel SLC NAND Flash Memory Market
Size and Forecast (2021 - 2031), Global and Regional Share, Trend, and Growth Opportunity Analysis Report Coverage: By Density (Above 8 GB, 8 GB, 4 GB, 2 GB, and 1 GB), Application (Industrial, Automotive, Consumer Electronics, Computers and IT, Communication, and Others), and Geography (North America, Europe, Asia Pacific, Middle East & Africa, and South & Central America)

Mar 2026
Serial SLC NAND Flash Memory Market
Size and Forecast (2021 - 2031), Global and Regional Share, Trend, and Growth Opportunity Analysis Report Coverage: By Density (1GB, 2GB, 4GB, 8GB, and Above 8GB); Application (Automotive, Industrial, Communication, Computers and IT, Consumer Electronics, and Others); and Geography (North America, Europe, Asia Pacific, Middle East & Africa, and South & Central America)

Mar 2026
Vertical Carousels ASRS Market
Size and Forecast (2021 - 2031), Global and Regional Share, Trend, and Growth Opportunity Analysis Report Coverage: By Type (Assembly, Distribution, Kitting, Order Picking, Storage, and Others), End use Industry (Automotive, Food and Beverages, Electronic and Semiconductors, E-Commerce, Chemicals, Aerospace, Retail, Pharmaceuticals and Others), and Geography (North America, Europe, Asia Pacific, Middle East and Africa, and South and Central America)

Mar 2026
Unit Load ASRS Market
Size and Forecast (2021 - 2031), Global and Regional Share, Trend, and Growth Opportunity Analysis Report Coverage: By Type (Assembly, Distribution, Kitting, Order Picking, Storage, Others), End Use Industry (Automotive, Food & Beverage, Electronic & Semiconductors, E-commerce, Chemicals, Aerospace, Retail, Pharmaceutical, Others), and Region (North America, Europe, Asia Pacific, Middle East and Africa, and South and Central America)



 Get Free Sample For
Get Free Sample For