Security Orchestration Market Analysis, Size, and Share by 2027
Security Orchestration Market to 2027 - Industry Analysis and Forecasts by Component (Software and Services); Deployment Type ( On-Premise and Cloud); Function (Network Security, Threat Intelligence, Compliance Management, Ticketing Solutions, End-Point Security and Others); Type of Enterprise (Small & Medium Scale and Large Scale); and End User (BFSI, Government, IT & Telecom, Manufacturing, Healthcare & Pharmaceuticals, and Others)
Historic Data: 2016-2017 | Base Year: 2018 | Forecast Period: 2019-2027- Report Date : Mar 2019
- Report Code : TIPTE100001073
- Category : Technology, Media and Telecommunications
- Status : Published
- Available Report Formats :


- No. of Pages : 160
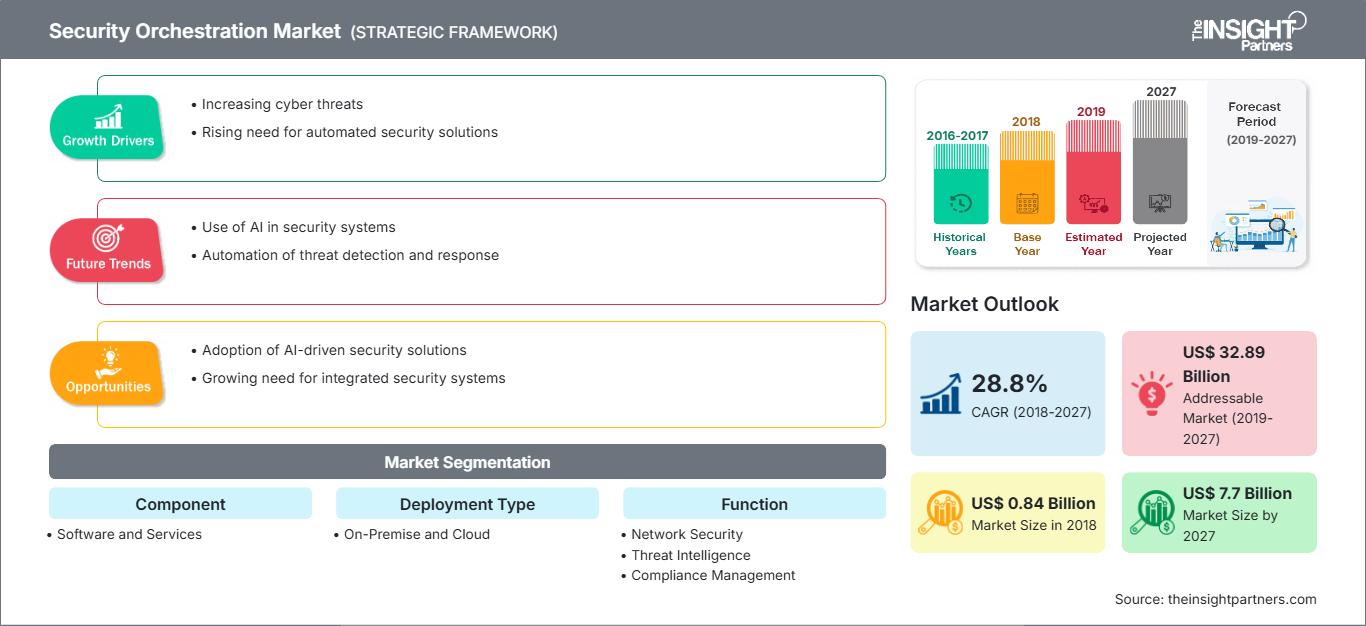
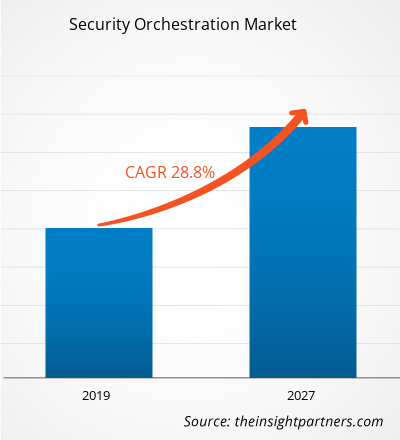
The security orchestration market was valued at US$ 0.84 Bn in 2018 and is expected to reach US$ 7.7 Bn by 2027 with an attractive CAGR growth rate of 28.8% in the forecast period.
Europe is the leading geographic segment in the security orchestration market and also, anticipated to be the highest revenue contributor throughout the forecast period, among the other geographies. By 2020 the region’s economic growth and competitiveness are expected to spur as the penetration of smart systems in its major social and economic sectors including, energy, transportation, public service, and healthcare will approach stability in the market. Furthermore, the pertained development and operation of these smart infrastructure is expected to subsequently contribute to evolved growth and employment of cyber-security measures.
Market Insights
Increase in number of cyber security threats coupled with stringent data security regulations by government agencies to boost the security orchestration market growth
Globally the number of number of connected devices has gained substantial volume which has led to unprecedented surge in data being generated daily. Subsequently, the cyber security threats have also risen in the past few years leading to efficient management and containment of the vulnerabilities across the entire organization. Moreover, in recent light of mass breach of data privacy coupled with growing awareness of cyber security awareness has influenced the government agencies into taking steps to ensure the cyber security compliances across different industry verticals. As a result, the global spending towards cyber security has gained significant momentum especially in the past few years.
Customize This Report To Suit Your Requirement
Get FREE CUSTOMIZATIONSecurity Orchestration Market: Strategic Insights
-
Get Top Key Market Trends of this report.This FREE sample will include data analysis, ranging from market trends to estimates and forecasts.
Growing number of alerts and incident response volume
The significant surge in number of connected devices coupled with growing number of internet users and low internet prices has witnessed unprecedented volume of data being generated daily. Moreover, the presence of large scaled networks and end-points creates a room for numerous potential vulnerabilities that require the attention of the security professionals and cyber security experts. As a result, the volume of alerts and events notification has risen significantly, which can be really challenging for the individuals.
End-user Insights
The global security orchestration market by end-user was led by BFSI sector. Banking, financial services, and insurance (BFSI) industries are more exposed to cyber-attacks due to the presence of huge financial and personal data of customers. In this sector, a high amount of sensitive data is generated and exchanged every day. There is growing volume and creation of endpoints and mobile devices in banks, credit card companies, and credit reporting institutions, thus, it becomes important for these industry verticals to secure their customer data. Currently, mobile service is the fundamental of banking for their employees, agents, and customers. Many of the cyber attackers are motivated by financial gain. Hence, BFSI industries are more inclined towards the adoption of security solution for the protection from malware and integrated app protection.
Function Insights
The security orchestration market by function is segmented into network security, threat intelligence, compliance management, ticketing solution, end-point security, and others. The end-point security is anticipated to lead the security orchestration market in 2027. The end-point security in security orchestration provides pre and post analysis of attacks, prevents data breaches in real time, and automatically orchestrate incident investigations and response. It provides orchestration, detection, investigation, remediation, prevention, and management console.
The players present in security orchestration market are mainly focusing towards product enhancements. By signing partnership, contracts, joint ventures, funding, and inaugurating new offices across the world permit the company maintain its brand name globally. Most of the initiative in security orchestration market were observed in North America and Europe regions, which have high density of orchestration related solutions. Few of the recent developments are listed below:
2019:CyberSponse announced integration of CyOPs SOAR platform with Polarity Memory Augmentation Platform. The integration is anticipated to help users to execute and escalate security orchestration and automation playbooks right from within Polarity.
2018:Oracle NetSuite announced series of new innovations to empower new business users and help the organizations to grow their revenues, expand the business with use of new commerce, financial management and analytics capabilities.
2018:Microsoft released an update for Windows Defender Advanced Threat Protection (ATP) that is expected to offer a quick response time during an attack. The new version includes features like advanced threat hunting, more powerful post-breach detection and response, and enhanced automation tools among other features.
Security Orchestration
Security Orchestration Market Regional InsightsThe regional trends influencing the Security Orchestration Market have been analyzed across key geographies.
Security Orchestration Market Report Scope
| Report Attribute | Details |
|---|---|
| Market size in 2018 | US$ 0.84 Billion |
| Market Size by 2027 | US$ 7.7 Billion |
| Global CAGR (2018 - 2027) | 28.8% |
| Historical Data | 2016-2017 |
| Forecast period | 2019-2027 |
| Segments Covered |
By Component
|
| Regions and Countries Covered |
North America
|
| Market leaders and key company profiles |
|
Security Orchestration Market Players Density: Understanding Its Impact on Business Dynamics
The Security Orchestration Market is growing rapidly, driven by increasing end-user demand due to factors such as evolving consumer preferences, technological advancements, and greater awareness of the product's benefits. As demand rises, businesses are expanding their offerings, innovating to meet consumer needs, and capitalizing on emerging trends, which further fuels market growth.
Global Security Orchestration Market – By Component
- Software
- Services
- Professional Service
- Managed Service
Global Security orchestration Market – By Deployment Type
- On-Premise
- Cloud
Global Security Orchestration Market – By Function
- Network Security
- Threat Intelligence
- Compliance Management
- Ticketing Solution
- End-point Security
- Others
Global Security Orchestration Market – By Enterprise Type
- Small & Medium Scaled
- Large Scaled
Global Security Orchestration Market – By End-user
- BFSI
- Government
- IT & Telecom
- Manufacturing
- Healthcare & Pharmaceuticals
- Others
Global Security Orchestration Market – By Geography
-
North America
- U.S.
- Canada
- Mexico
-
Europe
- France
- Germany
- UK
- Italy
- Spain
- Rest of Europe
-
Asia Pacific (APAC)
- India
- Australia
- China
- Japan
- Rest of APAC
-
Middle East & Africa (MEA)
- Saudi Arabia
- UAE
- South Africa
- Rest of MEA
-
South America (SAM)
- Brazil
- Rest of SAM
Company Profiles
- CyberSponse, Inc.
- DFLabs S.p.A.
- FireEye, Inc.
- Microsoft Corporation (Hexadite)
- Tufin
- Phantom Cyber Corporation (Splunk Inc.)
- Swimlane LLC
- Demisto, Inc.
- Siemplify Ltd.
- Cyberbit Ltd.
Ankita is a dynamic market research and consulting professional with over 8 years of experience across the technology, media, ICT, and electronics & semiconductor sectors. She has successfully led and delivered 100+ consulting and research assignments for global clients such as Microsoft, Oracle, NEC Corporation, SAP, KPMG, and Expeditors International. Her core competencies include market assessment, data analysis, forecasting, strategy formulation, competitive intelligence, and report writing.
Ankita is adept at handling complete project cycles—from pre-sales proposal design and client discussions to post-sales delivery of actionable insights. She is skilled in managing cross-functional teams, structuring complex research modules, and aligning solutions with client-specific business goals. Her excellent communication, leadership, and presentation abilities have enabled her to consistently deliver value-driven outcomes in fast-paced and evolving market environments.
- Historical Analysis (2 Years), Base Year, Forecast (7 Years) with CAGR
- PEST and SWOT Analysis
- Market Size Value / Volume - Global, Regional, Country
- Industry and Competitive Landscape
- Excel Dataset
Recent Reports
Testimonials
The Insight Partners' SCADA System Market report is comprehensive, with valuable insights on current trends and future forecasts. The team was highly professional, responsive, and supportive throughout. We are very satisfied and highly recommend their services.
RAN KEDEM Partner, Reali Technologies LTDsI requested a report on a very specific software market and the team produced the report in a few days. The information was very relevant and well presented. I then requested some changes and additions to the report. The team was again very responsive and I got the final report in less than a week.
JEAN-HERVE JENN Chairman, Future AnalyticaWe worked with The Insight Partners for an important market study and forecast. They gave us clear insights into opportunities and risks, which helped shape our plans. Their research was easy to use and based on solid data. It helped us make smart, confident decisions. We highly recommend them.
PIYUSH NAGPAL Sr. Vice President, High Beam GlobalThe Insight Partners delivered insightful, well-structured market research with strong domain expertise. Their team was professional and responsive throughout. The user-friendly website made accessing industry reports seamless. We highly recommend them for reliable, high-quality research services
YUKIHIKO ADACHI CEO, Deep Blue, LLC.This is the first time I have purchased a market report from The Insight Partners.While I was unsure at first, I visited their web site and felt more comfortable to take the risk and purchase a market report.I am completely satisfied with the quality of the report and customer service. I had several questions and comments with the initial report, but after a couple of dialogs over email with their analyst I believe I have a report that I can use as input to our strategic planning process.Thank you so much for taking the extra time and making this a positive experience.I will definitely recommend your service to others and you will be my first call when we need further market data.
JOHN SUZUKI President and Chief Executive Officer, Board Director, BK TechnologiesI wish to appreciate your support and the professionalism you displayed in the course of attending to my request for information regarding to infectious disease IVD market in Nigeria. I appreciate your patience, your guidance, and the fact that you were willing to offer a discount, which eventually made it possible for us to close a deal. I look forward to engaging The Insight Partners in the future, all thanks to the impression you have created in me as a result of this first encounter.
DR CHIJIOKE ONYIA MANAGING DIRECTOR, PineCrest Healthcare Ltd.Reason to Buy
- Informed Decision-Making
- Understanding Market Dynamics
- Competitive Analysis
- Identifying Emerging Markets
- Customer Insights
- Market Forecasts
- Risk Mitigation
- Boosting Operational Efficiency
- Strategic Planning
- Investment Justification
- Tracking Industry Innovations
- Aligning with Regulatory Trends





 Get Free Sample For
Get Free Sample For