Advanced Authentication Market Trends, Growth and Size - 2031
Advanced Authentication Market Size and Forecasts (2021 - 2031), Global and Regional Share, Trends, and Growth Opportunity Analysis Report Coverage: By Authentication Methods (Smart Cards, Biometrics, Mobile Smart Credentials, Tokens, User-based Public Key Infrastructure, Other); End User (BFSI, Healthcare, Government, Defense, IT and Telecom, Other) , and Geography (North America, Europe, Asia Pacific, and South and Central America)
Historic Data: 2021-2023 | Base Year: 2024 | Forecast Period: 2025-2031- Report Date : Mar 2026
- Report Code : TIPRE00021357
- Category : Electronics and Semiconductor
- Status : Upcoming
- Available Report Formats :


- No. of Pages : 150
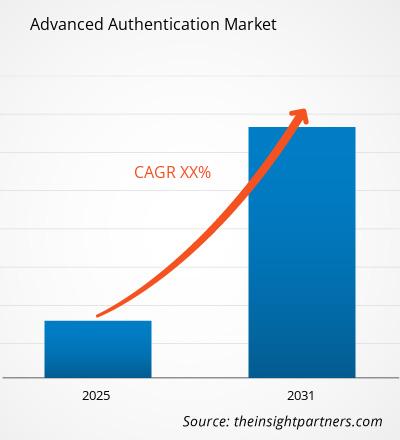
The Advanced Authentication Market is expected to register a CAGR of XX% from 2025 to 2031, with a market size expanding from US$ XX million in 2024 to US$ XX Million by 2031.
The report is categorized by Authentication Methods (Smart Cards, Biometrics, Mobile Smart Credentials, Tokens, User-based Public Key Infrastructure) and further analyzes the market based on End User (BFSI, Healthcare, Government, Defense, IT and Telecom). A comprehensive breakdown is provided at global, regional, and country levels for each of these key segments.
The report includes market size and forecasts across all segments, presenting values in USD. It also delivers key statistics on the current market status of leading players, along with insights into prevailing market trends and emerging opportunities.
Purpose of the Report
The report Advanced Authentication Market by The Insight Partners aims to describe the present landscape and future growth, top driving factors, challenges, and opportunities. This will provide insights to various business stakeholders, such as:
- Technology Providers/Manufacturers: To understand the evolving market dynamics and know the potential growth opportunities, enabling them to make informed strategic decisions.
- Investors: To conduct a comprehensive trend analysis regarding the market growth rate, market financial projections, and opportunities that exist across the value chain.
- Regulatory bodies: To regulate policies and police activities in the market with the aim of minimizing abuse, preserving investor trust and confidence, and upholding the integrity and stability of the market.
Advanced Authentication Market Segmentation
Authentication Methods
- Smart Cards
- Biometrics
- Mobile Smart Credentials
- Tokens
- User-based Public Key Infrastructure
End User
- BFSI
- Healthcare
- Government
- Defense
- IT and Telecom
Customizee This Report To Suit Your Requirement
Get FREE CUSTOMIZATIONAdvanced Authentication Market: Strategic Insights
-
Get Top Key Market Trends of this report.This FREE sample will include data analysis, ranging from market trends to estimates and forecasts.
Advanced Authentication Market Growth Drivers
- Elevating Security: Advanced Authentication Solutions for Businesses
- Seamless User Experience: The Future of Advanced Authentication Tech
- Driving Compliance: Advanced Authentication in a Regulatory Landscape
Advanced Authentication Market Future Trends
- Advanced Authentication Market's New Frontiers
- Embracing Security: Opportunities in Advanced Authentication Solutions
- Future-Proofing Business: The Rise of Advanced Authentication Technologies
Advanced Authentication Market Opportunities
- Seamless Security: The Rise of Biometric Authentication Solutions
- AI-Powered Identity Verification: A Game Changer for Online Safety
- Passwordless Future: Embracing Convenience in Digital Security
Advanced Authentication Market Regional Insights
The regional trends and factors influencing the Advanced Authentication Market throughout the forecast period have been thoroughly explained by the analysts at The Insight Partners. This section also discusses Advanced Authentication Market segments and geography across North America, Europe, Asia Pacific, Middle East and Africa, and South and Central America.
Advanced Authentication Market Report Scope
| Report Attribute | Details |
|---|---|
| Market size in 2024 | US$ XX million |
| Market Size by 2031 | US$ XX Million |
| Global CAGR (2025 - 2031) | XX% |
| Historical Data | 2021-2023 |
| Forecast period | 2025-2031 |
| Segments Covered |
By Authentication Methods
|
| Regions and Countries Covered |
North America
|
| Market leaders and key company profiles |
|
Advanced Authentication Market Players Density: Understanding Its Impact on Business Dynamics
The Advanced Authentication Market is growing rapidly, driven by increasing end-user demand due to factors such as evolving consumer preferences, technological advancements, and greater awareness of the product's benefits. As demand rises, businesses are expanding their offerings, innovating to meet consumer needs, and capitalizing on emerging trends, which further fuels market growth.
- Get the Advanced Authentication Market top key players overview
Key Selling Points
- Comprehensive Coverage: The report comprehensively covers the analysis of products, services, types, and end users of the Advanced Authentication Market, providing a holistic landscape.
- Expert Analysis: The report is compiled based on the in-depth understanding of industry experts and analysts.
- Up-to-date Information: The report assures business relevance due to its coverage of recent information and data trends.
- Customization Options: This report can be customized to cater to specific client requirements and suit the business strategies aptly.
The research report on the Advanced Authentication Market can, therefore, help spearhead the trail of decoding and understanding the industry scenario and growth prospects. Although there can be a few valid concerns, the overall benefits of this report tend to outweigh the disadvantages.
Naveen is an experienced market research and consulting professional with over 9 years of expertise across custom, syndicated, and consulting projects. Currently serving as Associate Vice President, he has successfully managed stakeholders across the project value chain and has authored over 100 research reports and 30+ consulting assignments. His work spans across industrial and government projects, contributing significantly to client success and data-driven decision-making.
Naveen holds an Engineering degree in Electronics & Communication from VTU, Karnataka, and an MBA in Marketing & Operations from Manipal University. He has been an active IEEE member for 9 years, participating in conferences, technical symposiums, and volunteering at both section and regional levels. Prior to his current role, he worked as an Associate Strategic Consultant at IndustryARC and as an Industrial Server Consultant at Hewlett Packard (HP Global).
- Historical Analysis (2 Years), Base Year, Forecast (7 Years) with CAGR
- PEST and SWOT Analysis
- Market Size Value / Volume - Global, Regional, Country
- Industry and Competitive Landscape
- Excel Dataset
Recent Reports
Testimonials
The Insight Partners' SCADA System Market report is comprehensive, with valuable insights on current trends and future forecasts. The team was highly professional, responsive, and supportive throughout. We are very satisfied and highly recommend their services.
RAN KEDEM Partner, Reali Technologies LTDsI requested a report on a very specific software market and the team produced the report in a few days. The information was very relevant and well presented. I then requested some changes and additions to the report. The team was again very responsive and I got the final report in less than a week.
JEAN-HERVE JENN Chairman, Future AnalyticaWe worked with The Insight Partners for an important market study and forecast. They gave us clear insights into opportunities and risks, which helped shape our plans. Their research was easy to use and based on solid data. It helped us make smart, confident decisions. We highly recommend them.
PIYUSH NAGPAL Sr. Vice President, High Beam GlobalThe Insight Partners delivered insightful, well-structured market research with strong domain expertise. Their team was professional and responsive throughout. The user-friendly website made accessing industry reports seamless. We highly recommend them for reliable, high-quality research services
YUKIHIKO ADACHI CEO, Deep Blue, LLC.This is the first time I have purchased a market report from The Insight Partners.While I was unsure at first, I visited their web site and felt more comfortable to take the risk and purchase a market report.I am completely satisfied with the quality of the report and customer service. I had several questions and comments with the initial report, but after a couple of dialogs over email with their analyst I believe I have a report that I can use as input to our strategic planning process.Thank you so much for taking the extra time and making this a positive experience.I will definitely recommend your service to others and you will be my first call when we need further market data.
JOHN SUZUKI President and Chief Executive Officer, Board Director, BK TechnologiesI wish to appreciate your support and the professionalism you displayed in the course of attending to my request for information regarding to infectious disease IVD market in Nigeria. I appreciate your patience, your guidance, and the fact that you were willing to offer a discount, which eventually made it possible for us to close a deal. I look forward to engaging The Insight Partners in the future, all thanks to the impression you have created in me as a result of this first encounter.
DR CHIJIOKE ONYIA MANAGING DIRECTOR, PineCrest Healthcare Ltd.Reason to Buy
- Informed Decision-Making
- Understanding Market Dynamics
- Competitive Analysis
- Identifying Emerging Markets
- Customer Insights
- Market Forecasts
- Risk Mitigation
- Boosting Operational Efficiency
- Strategic Planning
- Investment Justification
- Tracking Industry Innovations
- Aligning with Regulatory Trends



















 Get Free Sample For
Get Free Sample For