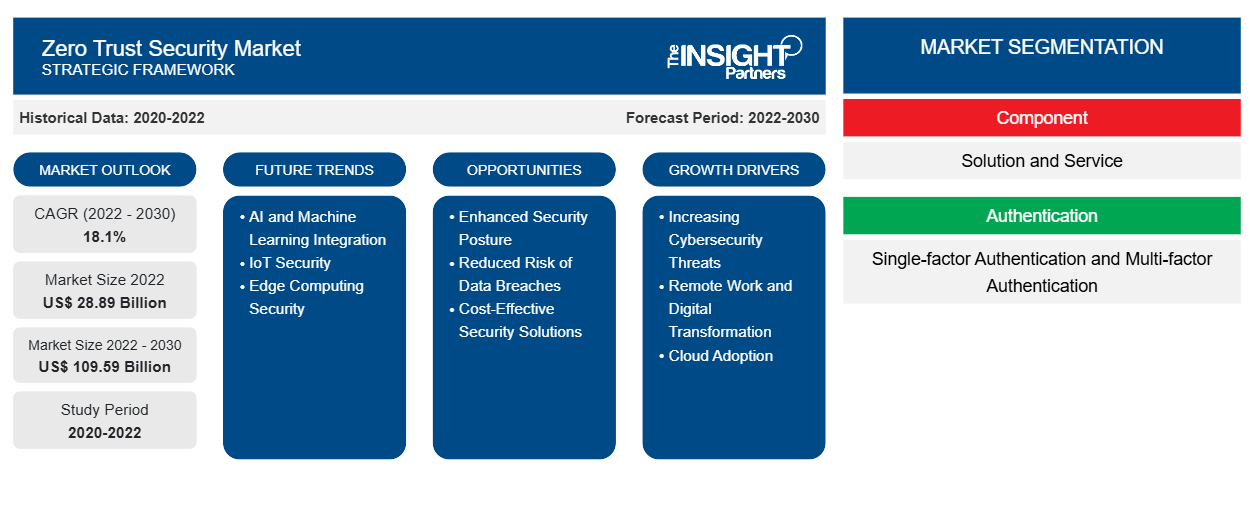
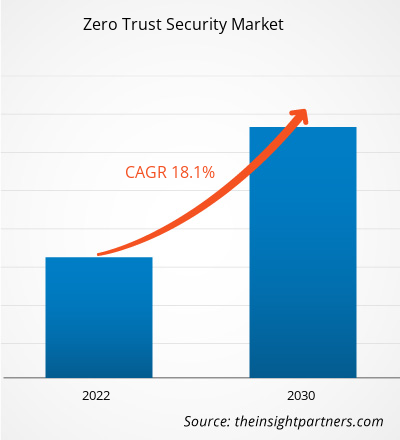
[Research Report] The zero trust security market size was valued at US$ 28.89 billion in 2022 and is expected to reach US$ 109.59 billion by 2030; it is estimated to record a CAGR of 18.1% from 2022 to 2030.
Zero Trust Security Market Analyst Perspective:
Identity and access management (IAM) is a crucial element of a zero trust security approach, as it aids organizations in ensuring that unauthorized users do not have access to sensitive resources. By deploying IAM systems, corporations can establish and impose policies for determining which person has access to what resources and can incessantly verify the identity of users and devices to safeguard security and ensure that they are approved to access specific resources. In addition, IAM systems can assist enterprises in tracking user access to resources and detect when unauthorized access or illegitimate activity is attempted. This can aid organizations in identifying and inhibiting probable security breaches; thus, it is an important asset for complying with regulatory requirements related to data privacy and security. Thus, with the appropriate IAM solution, corporations can establish zero trust authentication and authorization methods, as well as zero trust encryption for in-transit and at-rest data.
Zero Trust Security Market Overview:
The global zero trust security market is experiencing extensive growth and is estimated to continue expanding in the coming years. Zero trust is a framework that ensures the security of the infrastructure and data of an enterprise. It exclusively addresses the contemporary challenges of present-day business, including securing hybrid cloud environments, remote workers, and ransomware threats. The zero trust security market is moderately fragmented. Market players are expanding their business by employing various methods, such as product portfolio expansion, service expansion, mergers & acquisitions (M&A), and collaborations. In June 2023, AKITA, a leading technology zero trust and network security solutions provider, merged with odixa—a major provider of advanced malware prevention solutions. The merger is anticipated to enable the new company to offer advanced and comprehensive zero trust cybersecurity solutions to their clientele.
Customize This Report To Suit Your Requirement
You will get customization on any report - free of charge - including parts of this report, or country-level analysis, Excel Data pack, as well as avail great offers and discounts for start-ups & universities
Zero Trust Security Market: Strategic Insights
- Get Top Key Market Trends of this report.This FREE sample will include data analysis, ranging from market trends to estimates and forecasts.
Customize This Report To Suit Your Requirement
You will get customization on any report - free of charge - including parts of this report, or country-level analysis, Excel Data pack, as well as avail great offers and discounts for start-ups & universities
Zero Trust Security Market: Strategic Insights

- Get Top Key Market Trends of this report.This FREE sample will include data analysis, ranging from market trends to estimates and forecasts.
Zero Trust Security Market Driver:
Rise in Bring Your Own Device (BYOD) Fuels Zero Trust Security Market Growth
Many well-known data experts agree that the generated data will grow exponentially during the forecast period. Based on research from Seagate's Data Age 2025 report, the world's data sphere will reach 175 zettabytes by 2025. This development is attributed to the enormous increase in people working, studying, and using streaming platforms from home. Hence, such a change is expected to create lucrative opportunities for the zero trust security market players over the forecast period. Additionally, the IT infrastructure is expected to become more complicated and varied due to the Bring Your Own Device (BYOD) regulations, utilization of business apps, introduction of new platforms, Choose Your Own Device (CYOD) trends, and implementation of other technologies. The BYOD and CYOD trends are becoming increasingly common in business settings due to the rapid improvements in mobile computing. Hence, employees are able to access organizational data via mobile devices anytime, which increases employee productivity. Installation of zero trust solutions, for such instances, ensures that organizational data is secured and kept confidential. Such factors are strongly fueling the demand for solutions and services offered by the zero trust security market players.
Zero Trust Security Market Segmental Analysis:
The zero trust security market is categorized on the basis of component, authentication, deployment, organization size, application, and end use. Based on component, the zero trust security market is bifurcated into solution and service. In terms of authentication, the market is divided into single-factor authentication and multi-factor authentication. Based on deployment, the market is bifurcated into on-premise and cloud. Based on organization size, the market is bifurcated into SMEs and large enterprises. In terms of application, the market is segmented into endpoint, network, and others. Based on end use, the market is segmented into BFSI, e-commerce & retail, healthcare, IT & telecom, and others. By geography, the zero trust security market is segmented into North America, Europe, Asia Pacific (APAC), the Middle East & Africa (MEA), and South America (SAM).
Single-factor authentication simplifies zero-trust authentication by allowing users to access multiple resources and systems with a single set of credentials rather than requiring different login information for each system. It can enhance the user experience and reduce the risk of users choosing weak passwords, as well as diminish the risk of users recycling passwords across multiple systems. Multi-factor authentication might seem cumbersome to the user, but it is deemed more secure. By mandating multiple authentication factors, it aids organizations to ensure that only approved users can avail sensitive resources by making it harder for attackers to gain illicit access, even if they are succesful in obtaining a user’s password. It is often used in conjunction with other zero trust solutions, such as IAM systems, to provide an added layer of security.
Zero Trust Security Market Regional Analysis:
The development of data protection and cybersecurity laws in Asian countries is expanding significantly. As individuals become occupied in new digital reality via mobile handsets and the internet-of-things (IoT), there is an increase in government iniatiatives toward digital identity programs and invasive approaches to electronic surveillance. In this respect, the use of the General Data Protection Regulation (GDPR) and data protection rules in the region is gaining attention. For instance, the region has experienced significant steps in China. APAC is presumed to emerge as the fastest-growing region over the forecast period. The growing acceptance of mobile devices across businesses and IoT applications is primarily responsible for the market growth in the region. Furthermore, the growing adoption of bring your own device (BYOD) policies and cloud-based solutions is another factor contributing to the zero trust security market growth. Additionally, the growth in digital workplace trends and transformation in data centers is anticipated to boost zero trust security market growth over the forecast period.
Zero Trust Security Market Regional Insights
The regional trends and factors influencing the Zero Trust Security Market throughout the forecast period have been thoroughly explained by the analysts at Insight Partners. This section also discusses Zero Trust Security Market segments and geography across North America, Europe, Asia Pacific, Middle East and Africa, and South and Central America.
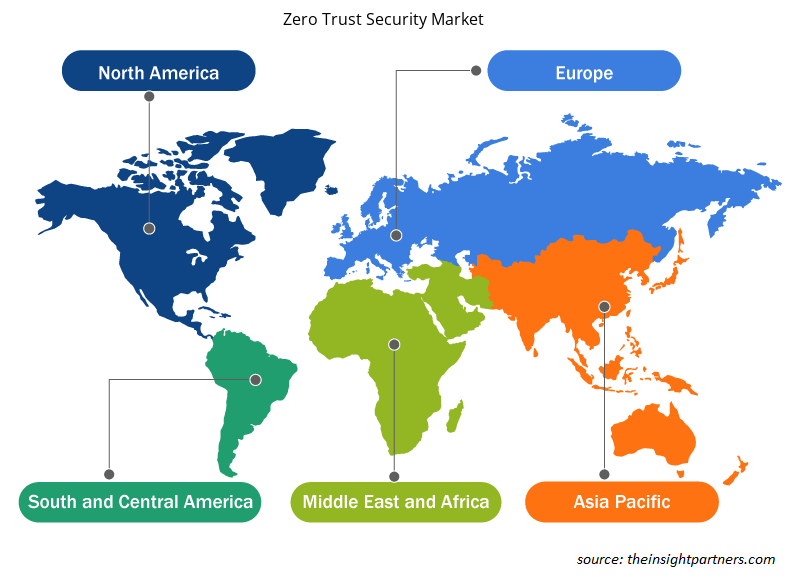
- Get the Regional Specific Data for Zero Trust Security Market
Zero Trust Security Market Report Scope
| Report Attribute | Details |
|---|---|
| Market size in 2022 | US$ 28.89 Billion |
| Market Size by 2030 | US$ 109.59 Billion |
| Global CAGR (2022 - 2030) | 18.1% |
| Historical Data | 2020-2022 |
| Forecast period | 2022-2030 |
| Segments Covered |
By Component
|
| Regions and Countries Covered | North America
|
| Market leaders and key company profiles |
Zero Trust Security Market Players Density: Understanding Its Impact on Business Dynamics
The Zero Trust Security Market market is growing rapidly, driven by increasing end-user demand due to factors such as evolving consumer preferences, technological advancements, and greater awareness of the product's benefits. As demand rises, businesses are expanding their offerings, innovating to meet consumer needs, and capitalizing on emerging trends, which further fuels market growth.
Market players density refers to the distribution of firms or companies operating within a particular market or industry. It indicates how many competitors (market players) are present in a given market space relative to its size or total market value.
Major Companies operating in the Zero Trust Security Market are:
- Akamai Technologies Inc
- Cato Networks Ltd.
- Check Point Software Technologies Ltd
- Cisco Systems Inc
- Fortinet Inc
Disclaimer: The companies listed above are not ranked in any particular order.
- Get the Zero Trust Security Market top key players overview
Zero Trust Security Market Key Player Analysis:
Akamai Technologies Inc, Cato Networks Ltd, Check Point Software Technologies Ltd, Cisco Systems Inc, Fortinet Inc, Microsoft Corporation, Okta Inc, Palo Alto Networks Inc, VMWare Inc, and Zscaler Inc are among the key zero trust security market players operating in the market. Several other major companies have been analyzed during this research study to get a holistic view of the zero trust security market ecosystem.
Zero Trust Security Market Recent Developments:
The zero trust security market players highly adopt inorganic and organic strategies. A few major zero trust security market developments are listed below:
- In August 2023, Check Point Software, a leading cybersecurity company, announced the acquisition of secure access service edge (SASE) and network security vendor, Perimeter 81, for US$ 490 million to enhance its offerings for security beyond the network perimeter. The former company plans to integrate the latter’s zero trust network access and rapid deployment technology into its existing Infinity product architecture.
- In March 2023, Hewlett Packard Enterprise announced its plan to acquire Israeli cyber startup, Axis Security. The latter company offers cloud-based Security Services Edge (SSE) solutions that enable access to corporate and public cloud resources.
Frequently Asked Questions
What is the estimated market size for the global zero trust security market in 2022?
The global zero trust security market was estimated to be US$ 28.89 billion in 2022 and is expected to grow at a CAGR of 18.1% during the period 2022 - 2030.
What are the driving factors impacting the global zero trust security market?
Increased demand for cloud, and rise in bring your own device (BYOD) trend are the major factors that propel the global zero trust security market.
What are the future trends of the global zero trust security market?
Growing adoption of automation in healthcare sector is expected to positively impact and play a significant role in the global zero trust security market in the coming years.
What is the incremental growth of the global zero trust security market during the forecast period?
The incremental growth expected to be recorded for the global zero trust security market during the forecast period is US$ 80.70 billion.
What will be the market size of the global zero trust security market by 2030?
The global zero trust security market is expected to reach US$ 109.59 billion by 2030.
Which are the key players holding the major market share of the global zero trust security market?
The key players holding majority shares in the global zero trust security market are Check Point Software, Cisco Systems, Fortinet, Palo Alto Networks, and Zscaler.
- Historical Analysis (2 Years), Base Year, Forecast (7 Years) with CAGR
- PEST and SWOT Analysis
- Market Size Value / Volume - Global, Regional, Country
- Industry and Competitive Landscape
- Excel Dataset
- Parking Meter Apps Market
- eSIM Market
- Advanced Distributed Management System Market
- Online Exam Proctoring Market
- Electronic Data Interchange Market
- Barcode Software Market
- Maritime Analytics Market
- Cloud Manufacturing Execution System (MES) Market
- Robotic Process Automation Market
- Digital Signature Market
Testimonials
Reason to Buy
- Informed Decision-Making
- Understanding Market Dynamics
- Competitive Analysis
- Identifying Emerging Markets
- Customer Insights
- Market Forecasts
- Risk Mitigation
- Boosting Operational Efficiency
- Strategic Planning
- Investment Justification
- Tracking Industry Innovations
- Aligning with Regulatory Trends
Yes! We provide a free sample of the report, which includes Report Scope (Table of Contents), report structure, and selected insights to help you assess the value of the full report. Please click on the "Download Sample" button or contact us to receive your copy.
Absolutely — analyst assistance is part of the package. You can connect with our analyst post-purchase to clarify report insights, methodology or discuss how the findings apply to your business needs.
Once your order is successfully placed, you will receive a confirmation email along with your invoice.
• For published reports: You’ll receive access to the report within 4–6 working hours via a secured email sent to your email.
• For upcoming reports: Your order will be recorded as a pre-booking. Our team will share the estimated release date and keep you informed of any updates. As soon as the report is published, it will be delivered to your registered email.
We offer customization options to align the report with your specific objectives. Whether you need deeper insights into a particular region, industry segment, competitor analysis, or data cut, our research team can tailor the report accordingly. Please share your requirements with us, and we’ll be happy to provide a customized proposal or scope.
The report is available in either PDF format or as an Excel dataset, depending on the license you choose.
The PDF version provides the full analysis and visuals in a ready-to-read format. The Excel dataset includes all underlying data tables for easy manipulation and further analysis.
Please review the license options at checkout or contact us to confirm which formats are included with your purchase.
Our payment process is fully secure and PCI-DSS compliant.
We use trusted and encrypted payment gateways to ensure that all transactions are protected with industry-standard SSL encryption. Your payment details are never stored on our servers and are handled securely by certified third-party processors.
You can make your purchase with confidence, knowing your personal and financial information is safe with us.
Yes, we do offer special pricing for bulk purchases.
If you're interested in purchasing multiple reports, we’re happy to provide a customized bundle offer or volume-based discount tailored to your needs. Please contact our sales team with the list of reports you’re considering, and we’ll share a personalized quote.
Yes, absolutely.
Our team is available to help you make an informed decision. Whether you have questions about the report’s scope, methodology, customization options, or which license suits you best, we’re here to assist. Please reach out to us at sales@theinsightpartners.com, and one of our representatives will get in touch promptly.
Yes, a billing invoice will be automatically generated and sent to your registered email upon successful completion of your purchase.
If you need the invoice in a specific format or require additional details (such as company name, GST, or VAT information), feel free to contact us, and we’ll be happy to assist.
Yes, certainly.
If you encounter any difficulties accessing or receiving your report, our support team is ready to assist you. Simply reach out to us via email or live chat with your order information, and we’ll ensure the issue is resolved quickly so you can access your report without interruption.














The List of Companies - Zero Trust Security Market
- Akamai Technologies Inc
- Cato Networks Ltd.
- Check Point Software Technologies Ltd
- Cisco Systems Inc
- Fortinet Inc
- Microsoft Corporation
- Okta Inc
- Palo Alto Networks Inc
- VMWare Inc
- Zscaler Inc






 Get Free Sample For
Get Free Sample For