Counter Cyber Terrorism Market Size, Trends, Shares, and Forecast - 2031
Counter Cyber Terrorism Market Size and Forecasts (2021 - 2031), Global and Regional Share, Trends, and Growth Opportunity Analysis Report Coverage: By Component (Solution, Service); Security Type (Network Security, Endpoint Security, Application Security, Cloud Security, Others); Deployment (On Premises, Cloud); Organization Size (SMEs, Large Enterprises); Vertical (BFSI, Government and Defense, Energy and Utilities, Healthcare, IT and Telecom, Manufacturing, Retail, Others) , and Geography (North America, Europe, Asia Pacific, and South and Central America)
Historic Data: 2021-2023 | Base Year: 2024 | Forecast Period: 2025-2031- Report Date : Apr 2026
- Report Code : TIPRE00017753
- Category : Technology, Media and Telecommunications
- Status : Upcoming
- Available Report Formats :


- No. of Pages : 150
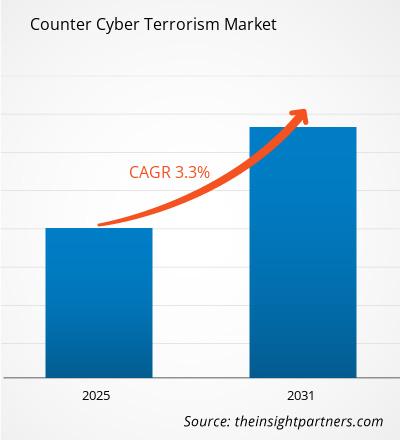
The Counter Cyber Terrorism Market is expected to register a CAGR of 3.3 % from 2025 to 2031, with a market size expanding from US$ XX million in 2024 to US$ XX Million by 2031.
The report is segmented by Component (Solution, Service); Security Type (Network Security, Endpoint Security, Application Security, Cloud Security, Others); Deployment (On Premises, Cloud); Organization Size (SMEs, Large Enterprises); Vertical (BFSI, Government and Defense, Energy and Utilities, Healthcare, IT and Telecom, Manufacturing, Retail, Others). The global analysis is further broken-down at regional level and major countries. The report offers the value in USD for the above analysis and segments
Purpose of the Report
The report Counter Cyber Terrorism Market by The Insight Partners aims to describe the present landscape and future growth, top driving factors, challenges, and opportunities. This will provide insights to various business stakeholders, such as:
- Technology Providers/Manufacturers: To understand the evolving market dynamics and know the potential growth opportunities, enabling them to make informed strategic decisions.
- Investors: To conduct a comprehensive trend analysis regarding the market growth rate, market financial projections, and opportunities that exist across the value chain.
- Regulatory bodies: To regulate policies and police activities in the market with the aim of minimizing abuse, preserving investor trust and confidence, and upholding the integrity and stability of the market.
Counter Cyber Terrorism Market Segmentation
Component
- Software
- Services
Security Type
- Network Security
- Endpoint Security
- Application Security
- Cloud Security
Deployment
- On Premises
- Cloud
Vertical
- BFSI
- Government and Defense
- Energy and Utilities
- Healthcare
- IT and Telecom
- Manufacturing
- Retail
Organization Size
- SMEs
- Large Enterprises
Customize This Report To Suit Your Requirement
Get FREE CUSTOMIZATIONCounter Cyber Terrorism Market: Strategic Insights
-
Get Top Key Market Trends of this report.This FREE sample will include data analysis, ranging from market trends to estimates and forecasts.
Counter Cyber Terrorism Market Growth Drivers
- Exponential Growth of Internet Interconnections: The exponentially growing number of interconnections of the internet has seen a corresponding growth in cyber attack cases, which often have devastating effects with devastating outcomes; and with more and more economic, commercial, and governmental activities moving online, the potential victim count increases, necessitating stronger defenses. Such interconnectivity demands organizations and governments to invest in more evolved cyber security solutions that protect critical infrastructure and sensitive information from cyber threats.
- Cyber Threat Evolution: The cyber terrorism methods evolve with the speed of technology, so do social networks, online transactions, cloud computing, and bring in new vulnerabilities that the cyber criminal has exploited. The emerging risks are continually prompted by evolving cyber threats, and hence require innovative counter-cyber terrorism strategies and technologies that can evolve to adapt to such risks and render them harmless in digital space environments.
- Increasing Reliance on Digital Infrastructure: As more businesses and governments adopt digital technologies and integrate critical systems into interconnected networks, the attack surface for cyber terrorists continues to expand. This increased reliance on cloud computing, IoT, and big data creates new vulnerabilities, making cybersecurity and counter-cyber terrorism solutions essential to protect sensitive infrastructure, communication systems, and data repositories. Organizations are investing in counter-cyber terrorism systems to safeguard these critical digital assets from potential cyber-attacks.
Counter Cyber Terrorism Market Future Trends
- Emphasis on Cyber Resilience:Organizations have switched from strictly preventing cyber attacks to concentrating more and more on cyber resilience. This prevents cyber attacks, but more importantly, develops the ability to quickly recover from them. That trend indicates that robust incident response plans and recovery strategies are such significant needs. Resilience provides organizations with the capacity to continue operations while minimizing the impacts of an attack by cyber terrorism.
- Integration of Cybersecurity with National Defense Systems: The convergence of cybersecurity and national defense systems is another important trend in the counter-cyber terrorism market. Governments are increasingly recognizing that cyberattacks can disrupt not only commercial and civilian operations but also national security infrastructure. As a result, defense agencies are incorporating cyber defense into their broader national security strategies, creating a more integrated approach to counter-cyber terrorism. This trend includes close collaboration between military, intelligence agencies, and cybersecurity experts to enhance the country's resilience against cyberterrorist threats.
Counter Cyber Terrorism Market Opportunities
- Advancements of Advanced AI and Machine Learning Solutions: The significant chance of combating cyberterrorism can be offered by integrating artificial intelligence and machine learning into cybersecurity. These technologies analyze big data to find patterns and anomalies that describe a cyber threat. AI-powered solutions automate the detection of threats, making a difference by improving the efficiency and effectiveness of cybersecurity measures, providing a more advanced proactive defense against complex cyber attacks.
- Growing Market Demand for Cybersecurity Services: Emerging markets also have substantial growth opportunities in the context of cybersecurity services. As these regions continue to digitize and encounter intensified cyber threats, comprehensive cybersecurity solutions are required. Thus, these cybersecurity firms can leverage this opportunity by identifying their service offerings based on the specific needs of such markets and help establish resilient digital infrastructures that protect against cyber terrorism.
Counter Cyber Terrorism Market Report Scope
| Report Attribute | Details |
|---|---|
| Market size in 2024 | US$ XX million |
| Market Size by 2031 | US$ XX Million |
| Global CAGR (2025 - 2031) | 3.3 % |
| Historical Data | 2021-2023 |
| Forecast period | 2025-2031 |
| Segments Covered |
By Component
|
| Regions and Countries Covered |
North America
|
| Market leaders and key company profiles |
|
Counter Cyber Terrorism Market Players Density: Understanding Its Impact on Business Dynamics
The Counter Cyber Terrorism Market is growing rapidly, driven by increasing end-user demand due to factors such as evolving consumer preferences, technological advancements, and greater awareness of the product's benefits. As demand rises, businesses are expanding their offerings, innovating to meet consumer needs, and capitalizing on emerging trends, which further fuels market growth.
Key Selling Points
- Comprehensive Coverage: The report comprehensively covers the analysis of products, services, types, and end users of the Counter Cyber Terrorism Market, providing a holistic landscape.
- Expert Analysis: The report is compiled based on the in-depth understanding of industry experts and analysts.
- Up-to-date Information: The report assures business relevance due to its coverage of recent information and data trends.
- Customization Options: This report can be customized to cater to specific client requirements and suit the business strategies aptly.
The research report on the Counter Cyber Terrorism Market can, therefore, help spearhead the trail of decoding and understanding the industry scenario and growth prospects. Although there can be a few valid concerns, the overall benefits of this report tend to outweigh the disadvantages.
Frequently Asked Questions
1. Exponential Growth of Internet Interconnections 2. Cyber Threat Evolution
Ankita is a dynamic market research and consulting professional with over 8 years of experience across the technology, media, ICT, and electronics & semiconductor sectors. She has successfully led and delivered 100+ consulting and research assignments for global clients such as Microsoft, Oracle, NEC Corporation, SAP, KPMG, and Expeditors International. Her core competencies include market assessment, data analysis, forecasting, strategy formulation, competitive intelligence, and report writing.
Ankita is adept at handling complete project cycles—from pre-sales proposal design and client discussions to post-sales delivery of actionable insights. She is skilled in managing cross-functional teams, structuring complex research modules, and aligning solutions with client-specific business goals. Her excellent communication, leadership, and presentation abilities have enabled her to consistently deliver value-driven outcomes in fast-paced and evolving market environments.
- Historical Analysis (2 Years), Base Year, Forecast (7 Years) with CAGR
- PEST and SWOT Analysis
- Market Size Value / Volume - Global, Regional, Country
- Industry and Competitive Landscape
- Excel Dataset
Recent Reports
Testimonials
The Insight Partners' SCADA System Market report is comprehensive, with valuable insights on current trends and future forecasts. The team was highly professional, responsive, and supportive throughout. We are very satisfied and highly recommend their services.
RAN KEDEM Partner, Reali Technologies LTDsI requested a report on a very specific software market and the team produced the report in a few days. The information was very relevant and well presented. I then requested some changes and additions to the report. The team was again very responsive and I got the final report in less than a week.
JEAN-HERVE JENN Chairman, Future AnalyticaWe worked with The Insight Partners for an important market study and forecast. They gave us clear insights into opportunities and risks, which helped shape our plans. Their research was easy to use and based on solid data. It helped us make smart, confident decisions. We highly recommend them.
PIYUSH NAGPAL Sr. Vice President, High Beam GlobalThe Insight Partners delivered insightful, well-structured market research with strong domain expertise. Their team was professional and responsive throughout. The user-friendly website made accessing industry reports seamless. We highly recommend them for reliable, high-quality research services
YUKIHIKO ADACHI CEO, Deep Blue, LLC.This is the first time I have purchased a market report from The Insight Partners.While I was unsure at first, I visited their web site and felt more comfortable to take the risk and purchase a market report.I am completely satisfied with the quality of the report and customer service. I had several questions and comments with the initial report, but after a couple of dialogs over email with their analyst I believe I have a report that I can use as input to our strategic planning process.Thank you so much for taking the extra time and making this a positive experience.I will definitely recommend your service to others and you will be my first call when we need further market data.
JOHN SUZUKI President and Chief Executive Officer, Board Director, BK TechnologiesI wish to appreciate your support and the professionalism you displayed in the course of attending to my request for information regarding to infectious disease IVD market in Nigeria. I appreciate your patience, your guidance, and the fact that you were willing to offer a discount, which eventually made it possible for us to close a deal. I look forward to engaging The Insight Partners in the future, all thanks to the impression you have created in me as a result of this first encounter.
DR CHIJIOKE ONYIA MANAGING DIRECTOR, PineCrest Healthcare Ltd.Reason to Buy
- Informed Decision-Making
- Understanding Market Dynamics
- Competitive Analysis
- Identifying Emerging Markets
- Customer Insights
- Market Forecasts
- Risk Mitigation
- Boosting Operational Efficiency
- Strategic Planning
- Investment Justification
- Tracking Industry Innovations
- Aligning with Regulatory Trends





 Get Free Sample For
Get Free Sample For