Privileged Access Management Solutions Market Analysis, Size, and Share by 2031
Privileged Access Management Solutions Market Size and Forecast (2021 - 2031), Global and Regional Share, Trend, and Growth Opportunity Analysis Report Coverage: By Offering (Solutions and Services), Deployment (On-Premise and Cloud), Enterprise Size (Large Enterprises and SMEs), End-Use Industry (BFSI, IT & Telecom, Healthcare, Energy & Utility, Retail & E-Commerce, Manufacturing, Government & Defense, and Others), and Geography
Historic Data: 2021-2022 | Base Year: 2023 | Forecast Period: 2024-2031- Report Date : Jun 2024
- Report Code : TIPRE00017221
- Category : Technology, Media and Telecommunications
- Status : Published
- Available Report Formats :


- No. of Pages : 206
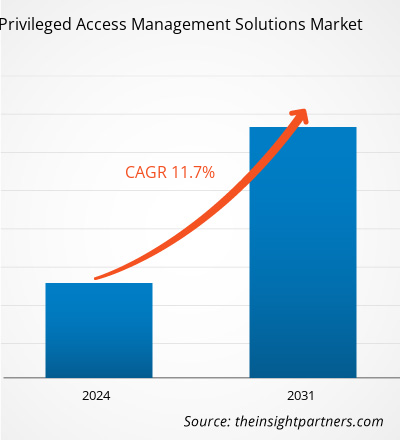
The privileged access management solutions market size is expected to reach US$ 5.95 billion by 2031 from US$ 2.46 billion in 2023. The privileged access management solutions market is estimated to record a CAGR of 11.7% from 2023 to 2031. The zero trust security model is likely to remain a key market trend.
Privileged Access Management Solutions Market Analysis
The increasing prevalence of cyberattacks targeting privileged accounts and credentials is driving the adoption of privileged access management solutions. Organizations are increasingly becoming aware of the need to safeguard their critical assets from unauthorized access and potential breaches. PAM solutions also play a crucial role in mitigating insider threats by implementing robust controls and monitoring privileged user actions. Furthermore, PAM solutions enable organizations to enforce adaptive access controls considering real-time contextual factors, granting appropriate access privileges based on the specific context. These solutions also assist organizations in meeting complex compliance requirements by offering risk management capabilities, maintaining detailed records of critical infrastructure activities, and facilitating audit-friendly IT environments.
The growing number of security breaches related to privileged access misuse has underscored the significance of robust privileged access management (PAM) solutions. These solutions help organizations reduce the attack surface by limiting privileged account membership and minimizing privileges. They also aid in mitigating insider threats through controls and monitoring privileged user activities. Moreover, PAM solutions enable organizations to enforce context-based access controls and enhance compliance with complex regulations.
Privileged Access Management Solutions Market Overview
Privileged access management (PAM) solutions are advanced security measures designed to safeguard organizations against cyber threats by actively monitoring, detecting, and preventing unauthorized access to critical resources. These solutions primarily focus on protecting privileged accounts, which possess elevated access privileges within an organization's systems and networks, making them prime targets for cybercriminals. PAM solutions utilize a combination of processes and technology to provide comprehensive visibility into the activities of privileged users and their use of privileged accounts.
Customizee This Report To Suit Your Requirement
Get FREE CUSTOMIZATIONPrivileged Access Management Solutions Market: Strategic Insights

-
Get Top Key Market Trends of this report.This FREE sample will include data analysis, ranging from market trends to estimates and forecasts.
Privileged Access Management Solutions Market Drivers and Opportunities
Increase in Number of Cyberattacks to Favor Market
In recent years, businesses are facing the continuous threat of cyberattacks. According to Embroker Insurance Services LLC, cyberattacks were considered the fifth top-rated risk in 2020, and cases continue to rise with technological advancements. Computer malware, data breaches, and denial of service (DoS) are a few examples of cyberattacks. During the COVID-19 pandemic, cybercriminals took advantage of misaligned networks as businesses were shifting to remote working environments. According to OneLogin, cybercrime costs more than US$ 1 trillion worldwide, as 37% of organizations were affected by ransomware and 61% were affected by malware attacks in 2020. Between 2019 and 2020, cyberattacks in the US increased by 139% as the country registered 145.2 million cases in Q3 2020. Malware attacks increased by 358% in 2020 compared to 2019. Similarly, according to the Clusit Report, cyberattacks across the globe increased by 10% in 2021 compared to the previous year. For instance, according to AAG, the UK had the highest number of cybercrime victims per million internet users (4,783 users) in 2022, an increase of 40% over 2020 figures. The average cost of a cyber breach was US$ 4.35 million in 2022, and it is predicted that this value is expected to reach US$ 10.5 trillion by 2025.
Cyber threats are considered a major concern as various organizations continue to operate in a digital environment. They have serious consequences for individuals, corporations, and governments. The rise in the number of cyberattacks has increased the importance of cybersecurity to safeguard critical infrastructures and to ensure the safety of individuals and organizations. Organizations are increasingly becoming aware of the need to safeguard their critical assets from unauthorized access and potential breaches. Thus, the increasing number of cyberattacks is a significant factor propelling the growth of the privileged access management (PAM) solutions market.
Emergence of Intelligence-Based Privileged Access Management Solutions
Intelligence-based PAM enables risk-based access control, where access decisions are based on risk assessments. Factors such as user roles, privileges, and contextual information are evaluated to determine the level of risk associated with a specific access request. This allows organizations to implement dynamic access controls that adapt to changing risk profiles. Intelligence-based PAM solutions can automate responses to security incidents or policy violations. For instance, if an unauthorized user attempts to access a privileged account, the solution can automatically block the access attempt and notify the security team. Intelligence-based PAM solutions continuously monitor privileged access activities in real-time. This proactive monitoring helps organizations detect suspicious or unauthorized behavior and respond to potential security threats before they escalate. Intelligence-based PAM also enables adaptive access policies that dynamically adjust based on contextual information. For instance, if a user's behavior indicates a higher risk, the solution can enforce stricter access controls or require additional authentication measures. Thus, the emergence of intelligence-based PAM solutions is anticipated to provide significant growth opportunities to the privileged access management (PAM) solutions market.
Privileged Access Management Solutions Market Report Segmentation Analysis
Key segments that contributed to the derivation of the privileged access management solutions market analysis are offering, deployment, enterprise size, and end-use industry.
- Based on offering, the market is segmented into solutions and services. The solution segment held a larger market share in 2023.
- By deployment, the market is bifurcated into cloud and on premise. The cloud segment dominated the market in 2023.
- In terms of enterprise size, the market is bifurcated into large enterprises and SMEs. The large enterprises segment dominated the market in 2023.
- Based on end-use industry, the market is segmented into BFSI, IT & telecom, healthcare, energy & utility, retail & ecommerce, manufacturing, government & defense, and others. The BFSI segment dominated the market in 2023.
Privileged Access Management Solutions Market Share Analysis by Geography
- The privileged access management solutions market is segmented into five major regions: North America, Europe, Asia Pacific (APAC), the Middle East & Africa (MEA), and South & Central America. North America dominated the market in 2023, followed by Europe and APAC.
- North America is one of the fastest-growing regions in terms of both technological innovations and the adoption of advanced technologies. With the increasing penetration of digitization in various industries, privileged access management solutions have become a vital component for businesses in North America to establish security measures. With the increasing penetration of digitization in various industries, PAM solutions have become a vital component of business. In addition, the region is home to market players such as IBM Corporation, Microsoft, Broadcom Inc., Fortinet Inc., and One Identity.
Privileged Access Management Solutions Market Regional Insights
The regional trends and factors influencing the Privileged Access Management Solutions Market throughout the forecast period have been thoroughly explained by the analysts at The Insight Partners. This section also discusses Privileged Access Management Solutions Market segments and geography across North America, Europe, Asia Pacific, Middle East and Africa, and South and Central America.
Privileged Access Management Solutions Market Report Scope
| Report Attribute | Details |
|---|---|
| Market size in 2023 | US$ 2.46 Billion |
| Market Size by 2031 | US$ 5.95 Billion |
| Global CAGR (2023 - 2031) | 11.7% |
| Historical Data | 2021-2022 |
| Forecast period | 2024-2031 |
| Segments Covered |
By Offering
|
| Regions and Countries Covered |
North America
|
| Market leaders and key company profiles |
|
Privileged Access Management Solutions Market Players Density: Understanding Its Impact on Business Dynamics
The Privileged Access Management Solutions Market is growing rapidly, driven by increasing end-user demand due to factors such as evolving consumer preferences, technological advancements, and greater awareness of the product's benefits. As demand rises, businesses are expanding their offerings, innovating to meet consumer needs, and capitalizing on emerging trends, which further fuels market growth.
- Get the Privileged Access Management Solutions Market top key players overview
Privileged Access Management Solutions Market News and Recent Developments
The privileged access management solutions market is evaluated by gathering qualitative and quantitative data post primary and secondary research, which includes important corporate publications, association data, and databases. A few of the developments in the privileged access management solutions market are listed below:
- CyberArk, the identity security company, announced that FM Logistic, a global supply chain management service, selected the CyberArk Identity Security Platform to secure tens of thousands of identities around the world and provide a secure foundation for its digital transformation and information security. To streamline processes and improve productivity, FM Logistics began a major digital transformation initiative, including a cloud migration project. Its existing identity management solution, however, was labor-intensive when managing privileged identities and not compatible with its cloud migration efforts. The company needed a solution to reduce complexity, simplify and automate its identity lifecycle management, provide privileged access management, and integrate with their cloud migration.
(Source: CyberArk, Press Release, May 2024)
- IBM unveiled its new security suite designed to unify and accelerate the security analyst experience across the full incident lifecycle. The IBM Security QRadar Suite represents a major evolution and expansion of the QRadar brand, spanning all core threat detection, investigation, and response technologies, with significant investment in innovations across the portfolio.
(Source: IBM, Press Release, April 2023)
Privileged Access Management Solutions Market Report Coverage and Deliverables
The "Privileged Access Management Solutions Market Size and Forecast (2021–2031)" provides a detailed analysis of the market covering the areas mentioned below:
- Privileged access management solutions market size and forecast at global, regional, and country levels for all the key market segments covered under the scope
- Privileged access management solutions market trends as well as market dynamics such as drivers, restraints, and key opportunities
- Detailed PEST and SWOT analysis
- Privileged access management solutions market analysis covering key market trends, global and regional framework, major players, regulations, and recent market developments
- Industry landscape and competition analysis covering market concentration, heat map analysis, prominent players, and recent developments for the privileged access management solutions market
- Detailed company profiles
Frequently Asked Questions
Ankita is a dynamic market research and consulting professional with over 8 years of experience across the technology, media, ICT, and electronics & semiconductor sectors. She has successfully led and delivered 100+ consulting and research assignments for global clients such as Microsoft, Oracle, NEC Corporation, SAP, KPMG, and Expeditors International. Her core competencies include market assessment, data analysis, forecasting, strategy formulation, competitive intelligence, and report writing.
Ankita is adept at handling complete project cycles—from pre-sales proposal design and client discussions to post-sales delivery of actionable insights. She is skilled in managing cross-functional teams, structuring complex research modules, and aligning solutions with client-specific business goals. Her excellent communication, leadership, and presentation abilities have enabled her to consistently deliver value-driven outcomes in fast-paced and evolving market environments.
- Historical Analysis (2 Years), Base Year, Forecast (7 Years) with CAGR
- PEST and SWOT Analysis
- Market Size Value / Volume - Global, Regional, Country
- Industry and Competitive Landscape
- Excel Dataset
Recent Reports
Related Reports
Testimonials
The Insight Partners' SCADA System Market report is comprehensive, with valuable insights on current trends and future forecasts. The team was highly professional, responsive, and supportive throughout. We are very satisfied and highly recommend their services.
RAN KEDEM Partner, Reali Technologies LTDsI requested a report on a very specific software market and the team produced the report in a few days. The information was very relevant and well presented. I then requested some changes and additions to the report. The team was again very responsive and I got the final report in less than a week.
JEAN-HERVE JENN Chairman, Future AnalyticaWe worked with The Insight Partners for an important market study and forecast. They gave us clear insights into opportunities and risks, which helped shape our plans. Their research was easy to use and based on solid data. It helped us make smart, confident decisions. We highly recommend them.
PIYUSH NAGPAL Sr. Vice President, High Beam GlobalThe Insight Partners delivered insightful, well-structured market research with strong domain expertise. Their team was professional and responsive throughout. The user-friendly website made accessing industry reports seamless. We highly recommend them for reliable, high-quality research services
YUKIHIKO ADACHI CEO, Deep Blue, LLC.This is the first time I have purchased a market report from The Insight Partners.While I was unsure at first, I visited their web site and felt more comfortable to take the risk and purchase a market report.I am completely satisfied with the quality of the report and customer service. I had several questions and comments with the initial report, but after a couple of dialogs over email with their analyst I believe I have a report that I can use as input to our strategic planning process.Thank you so much for taking the extra time and making this a positive experience.I will definitely recommend your service to others and you will be my first call when we need further market data.
JOHN SUZUKI President and Chief Executive Officer, Board Director, BK TechnologiesI wish to appreciate your support and the professionalism you displayed in the course of attending to my request for information regarding to infectious disease IVD market in Nigeria. I appreciate your patience, your guidance, and the fact that you were willing to offer a discount, which eventually made it possible for us to close a deal. I look forward to engaging The Insight Partners in the future, all thanks to the impression you have created in me as a result of this first encounter.
DR CHIJIOKE ONYIA MANAGING DIRECTOR, PineCrest Healthcare Ltd.Reason to Buy
- Informed Decision-Making
- Understanding Market Dynamics
- Competitive Analysis
- Identifying Emerging Markets
- Customer Insights
- Market Forecasts
- Risk Mitigation
- Boosting Operational Efficiency
- Strategic Planning
- Investment Justification
- Tracking Industry Innovations
- Aligning with Regulatory Trends



















 Get Free Sample For
Get Free Sample For